...
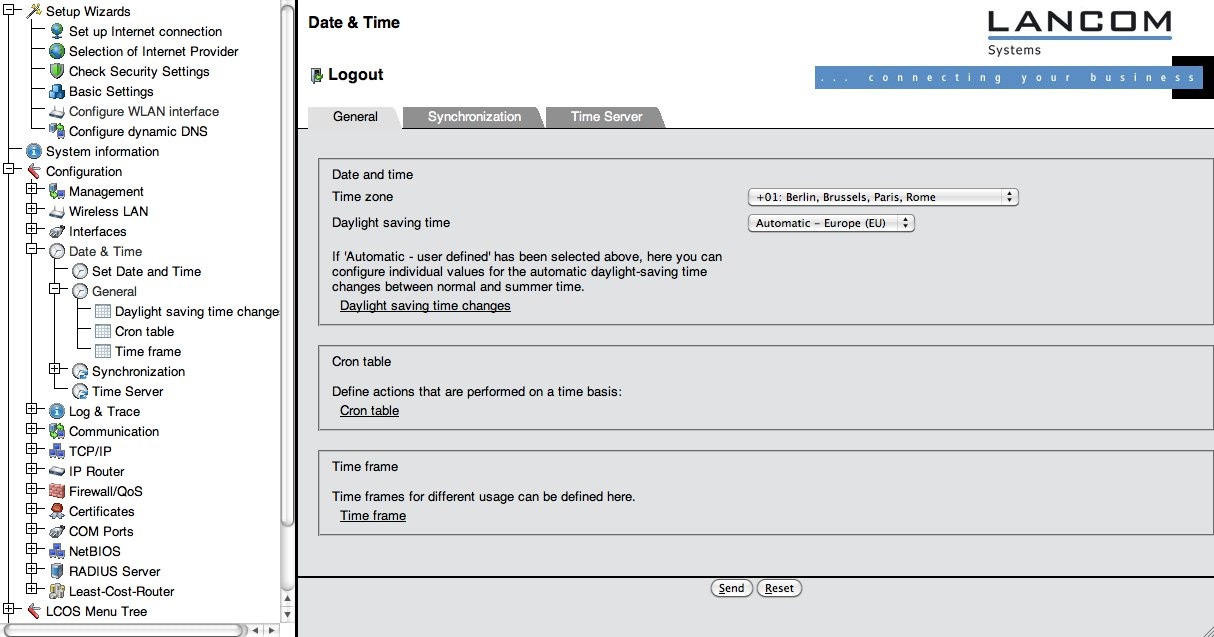
The Access point needs to be synchronised with a NTP or SNTP time server (which was set up using the wizard), which requires correct timezone settings. Click on "Configuration" -> "Date & Time" -> "General". and verify that the correct time zone and dayight saving time settings are set (see screenshot).
B.2.3 Logging
...
<ac:structured-macro ac:name="unmigrated-wiki-markup" ac:schema-version="1" ac:macro-id="0b08b1c60d0c75ef-1a8c30e8-43e74dbc-a6d3b9b2-8263cdb809efeaf53820086b"><ac:plain-text-body><![CDATA[ | AUTH | Notice | [WLAN-1] Associated WLAN station 64:b9:e8:a0:2e:a4 [] | ]]></ac:plain-text-body></ac:structured-macro> |
<ac:structured-macro ac:name="unmigrated-wiki-markup" ac:schema-version="1" ac:macro-id="d4bdaec2d102b195-7b472473-4bc449a7-89cab278-eeec77bc1881d549c7059290"><ac:plain-text-body><![CDATA[ | AUTH | Notice | [WLAN-1] WLAN station 64:b9:e8:a0:2e:a4 [] authenticated via 802.1x [user name is certuser-2010-001@restena.lu] | ]]></ac:plain-text-body></ac:structured-macro> |
<ac:structured-macro ac:name="unmigrated-wiki-markup" ac:schema-version="1" ac:macro-id="029277ebf2fc0272-6c9031f2-489c4230-9f908e0c-5f32ce011f1955ab7d105271"><ac:plain-text-body><![CDATA[ | AUTH | Notice | [WLAN-1] Key handshake with peer 64:b9:e8:a0:2e:a4 successfully completed | ]]></ac:plain-text-body></ac:structured-macro> |
<ac:structured-macro ac:name="unmigrated-wiki-markup" ac:schema-version="1" ac:macro-id="d30e98b13d92b135-5e25e04e-4fe548ac-8a58a582-50b9eac356482fe4e3d24f1e"><ac:plain-text-body><![CDATA[ | AUTH | Notice | [WLAN-1] Connected WLAN station 64:b9:e8:a0:2e:a4 [] | ]]></ac:plain-text-body></ac:structured-macro> |
<ac:structured-macro ac:name="unmigrated-wiki-markup" ac:schema-version="1" ac:macro-id="5437041eafdf0292-d0687208-42074bfa-8d44ac63-a1675425453c12842cc0e1fc"><ac:plain-text-body><![CDATA[ | AUTH | Notice | [WLAN-1] Determined IPv4 address for station 64:b9:e8:a0:2e:a4 []: 158.64.3.24 | ]]></ac:plain-text-body></ac:structured-macro> |
<ac:structured-macro ac:name="unmigrated-wiki-markup" ac:schema-version="1" ac:macro-id="42555ea2c768567e-bc31705a-4b24427f-9c4d8bc5-5cd1af2e7968390feeca04ff"><ac:plain-text-body><![CDATA[ | AUTH | Notice | [WLAN-1] Determined IPv6 address for station 64:b9:e8:a0:2e:a4 []: 2001:0a18:0000:0403:66b9:e8ff:fea0:2ea4 | ]]></ac:plain-text-body></ac:structured-macro> |
<ac:structured-macro ac:name="unmigrated-wiki-markup" ac:schema-version="1" ac:macro-id="ccd29b5b75758509-757a25e9-4133423b-a9f9b41e-e38dc118535f53c5c81eeeff"><ac:plain-text-body><![CDATA[ | AUTH | Notice | [WLAN-1] Determined IPv6 address for station 64:b9:e8:a0:2e:a4 []: fe80:0000:0000:0000:66b9:e8ff:fea0:2ea4 | ]]></ac:plain-text-body></ac:structured-macro> |
<ac:structured-macro ac:name="unmigrated-wiki-markup" ac:schema-version="1" ac:macro-id="02575c086cf87842-e5ef004a-48554f34-98efa43d-1c7472b02a4b1ceb550e0b55"><ac:plain-text-body><![CDATA[ | AUTH | Notice | [WLAN-1] Disassociated WLAN station 64:b9:e8:a0:2e:a4 [] due to station request (Disassociated because sending station is leaving BSS | ]]></ac:plain-text-body></ac:structured-macro> |
...
A recurring question is "Why is Client EAP method irrelevant?" The answer is: this setting refers to which authentication method the access point should use when it is in Client mode (i.e. it acts as a supplicant to connect to another access point). When in Access Point mode, its role is by design limited to transparently pass all authentication methods to a RADIUS server.
B.2.6
...
If RADIUS accounting for the eduroam SSID shall be enabled, you must configure a RADIUS server to receive
the accounting messages:
- Select Expert Configuration>Setup – WLAN – RADIUS-Accounting and complete the server details:
- Afterwards, activate the actual RADIUS Accounting reporting under Expert Configuration>Setup –
Interfaces – WLAN – Network – RADIUS-Accounting
...
Using RadSec instead of RADIUS (optional)
LANCOM devices have a RadSec client built-in. It can be used instead of standard RADIUS for the uplink to an
IdP.
To use RadSec, you must have been given a eduroam Service Provider X.509 certificate from your NRO. First,
upload this certificate and the eduGAIN CA certificate (which can be downloaded athttp://sca.edugain.org/cacert/eduGAINCA.pem) via the device's "File Upload" menu:
Then, go to Expert Configuration>Setup>IEEE802.1X>RADIUS Server and set the Protocol option to
RADSEC:
The same option is also present in the RADIUS Accounting server menu that was discussed above. When
RadSec is to be used, we strongly suggest to use it for both authentication and accounting.