DRAFT
The work item
- About Trust Over IP and Identity Wallets
The Trust over IP (ToIP) Foundation is an independent project hosted at the Linux Foundation, working with pan-industry support from leading organizations around the world. Its mission is to provide a robust, common standard and complete architecture for Internet-scale digital trust. The ToIP Foundation has grown rapidly to over 300 member organizations and individuals, and it has doubled from four to eight Working Groups, with over a dozen deliverables slated for release by the end of 2021
[1]
- Relationship Between ToIP and Identity Wallets
The ToIP model was originally inspired on digital identity wallets and agents. The focus has been on secure key pair generation and storage along with secure verifiable credential exchange and storage. However, the scope is steadily expanding to be inclusive of other decentralized identity stack architectures and protocols [2].The ToIP Foundation aims to build solutions that support the technical interoperability of blockchains, identity wallets, and verifiable credentials. This interoperability is a critical prerequisite for mass adoption and to enable the trusted exchange of data for everyone, everywhere.
- EU Digital Identity Wallet Initiative
The surge of interest in decentralized digital trust infrastructure has been fueled by the June 2021 announcement of the EU Digital Identity Wallet initiative. This initiative, along with Apple and Google's announcements about beginning to accept digitally-signed credentials in their proprietary digital wallets, has further propelled the interest in decentralized digital trust infrastructure[1]
- Our Mission
In GEANT we are trying to find the best solution of developing Wallet or contributing in wallet development to manage VC in research and education arena.
Transformative aspects
An essential Question is how is our contribution with EUDI.
Technology development in hardware and software affect the wallets.
‘Consent’ thema should be considered. If the wallet and VC are available, how the wallet can support users to protect them from extra revealing id attributes.
Opportunities
The major and transformative Question is, Is it really needed that a new wallet get developed? Or we could probably develop an entity that could be importable to almost every type of wallets? Into identity wallets, currency wallets,smartphone wallet,travel once or etc. And the next Question is , is it really possible without developing wallet? How big is challenging or dependency to other wallets.
We should always be aware of the progress on EU Digital Identity Wallet Consortium WP3. EWC WP3 covers the Reference Wallet integration as well as development of PID and ODI Credentials. Moreover, B2B test scenarios needed for additional testing of the PID/ODI combination are also developed in WP3. ODI stands for Organizational Digital Identity. An ODI wallet is a wallet software for legal entities and represents a stand-alone legal body.
We should also pay attention to DC4EU, specially WP7 led by SUNET [3]
In distributed ecosystem, wallets are the strategic points and its provider still has essential role. Because, all sensitive data are partially or completely available for wallet providers.
In a holistic view almost, all benefit of a central identity system can transfer to wallet, unless some regulations restrict the availability and access to data. For example: Statistics and analysis of user behavior.
Other opportunities e.g. Delivering the current status of a student not just a verifiable credential after graduation. It could be helpful by looking for master-job or any type of student job.
Risks
Here are some of the potential risks associated with digital ID wallets:
- Security Breaches: One of the primary risks is the potential for security breaches. If your digital ID wallet is compromised, an attacker may gain access to sensitive personal information, such as your driver’s license, passport, or other forms of identification.
- Identity Theft: If a malicious actor gains access to your digital ID wallet, they could use your identity to commit various forms of fraud and identity theft. This could have serious consequences for your financial and personal well-being.
- Data Privacy Concerns: Storing personal identification documents and data in a digital ID wallet means that this information is potentially accessible to service providers and the wallet provider itself. Users must trust these entities to protect their data adequately.
- Loss of Device: If you lose your mobile device or the device containing your digital ID wallet is stolen, there’s a risk that the thief could misuse your digital ID and access your accounts or impersonate you.
- Biometric Data Vulnerabilities: Many digital ID wallets use biometric authentication methods, such as fingerprint or facial recognition. These can be vulnerable to spoofing or hacking if not properly secured.
- Phishing and Social Engineering: Attackers may attempt to trick you into revealing your digital ID wallet credentials through phishing emails, fake websites, or social engineering attacks.
- Incompatibility and Interoperability Issues: Different regions and organizations may use different standards and technologies for digital ID. Compatibility issues could arise if your digital ID wallet is not accepted or recognized by certain entities.
- Regulatory and Legal Issues: The legal framework around digital ID is still evolving in many places. There may be regulatory changes or legal disputes that impact the use and security of digital ID wallets.
- Dependency on Technology: Relying on a digital ID wallet means that you’re dependent on technology and the infrastructure that supports it. Technical issues, outages, or system failures could temporarily prevent you from accessing your digital ID.[4]
- Technical Problems: Technical issues, such as system failures or connectivity issues, can prevent users from accessing their digital wallet accounts, making payments and accessing funds difficult.
- Limited Acceptance: Because digital wallets are not accepted everywhere, users may encounter situations in which they are unable to make payments using their digital wallets.
- Hidden fees: Some digital wallets may charge hidden fees, such as transaction fees, foreign exchange fees, or account maintenance fees. Users should review their digital wallet provider's fee schedule to ensure they understand the charges associated with using the platform. [5]
- No insurance by misusing or mistake. It is more related to currency wallet but for identity there such shortage too.
DRAFT
Subchapter | Description | Notes relevant to many/most T7 work items |
|---|---|---|
| The work item | a brief description of the topic at hand, map it to "our world". You may get inspiration from the corresponding ToIP description. | (individual) |
| Transformative aspects | What will potentially change with respect to our current way of delivering value in general? And what will change with a particular view to our ecosystem? Include a critical review of our existing ecosystem services and the nature of potential impact on them. |
|
| Opportunities | Describe use cases in our ecosystem that could potentially benefit from an emerging DI ecosystem Describe assumptions / requirements towards other players / outcomes etc. to make it deliver value to our ecosystem Describe actions we need to fulfil as a community (ecosystem) to get such value delivered to our ecosystem Might this make it easier for NRENs to participate in the ecosystem with less effort? |
|
| Risks | Describe potential situations or actions of other important stakeholders leading to a failure to deliver value to our ecosystem This could be linked to external developments but also to our inability to fulfil above actions or to get consensus in our own ecosystem |
|
| Engagements, projects | Describe (crowdsourced within our group) prior or ongoing activities in our ecosystem relevant to the topic at hand by NRENs and GÉANT |
|
| Recommendations | Recommendations towards NRENs (and their community), GÉANT and "the research community" |
|
References
[1]https://trustoverip.org/about/about/
[2] https://trustoverip.org/blog/2022/07/13/identity-week-2022-recap/
[3]About DC4EU, 2024
[4] DIGITAL IDENTITY WALLET BENEFITS AND RISKS
[5] The Advantages and Risks of Moving Your Money to a Digital Wallet
A digital identity wallet is a secure, encrypted database that collects and holds keys, identifiers, and verifiable credentials (VCs). The wallet is also a digital address book, collecting and maintaining its controller’s many relationships. The wallet is coupled with a software agent that speaks the protocols necessary to engage with others. Sometimes, we’ve used wallet as a shorthand for both wallet and agent, not distinguishing carefully between them. But here, we’ll be more specific about which tool performs which actions. Alice’s digital wallet might contain many things that she, in her capacity as controller, needs to store securely, including:
- Decentralized identifiers she has created or received, including public DIDs, peer DIDs, and KERI identifiers
- The backing store (or key event log) she uses to manage peer relationships
- Keys related to DIDs but perhaps others as well; SSH keys, for example, could be securely managed in a digital wallet
- PKI digital certificates and the private keys associated with them
- Keys and addresses for cryptocurrency
- VCs that Alice holds
- Receipts, warranties, and titles (some as VCs)
- PDFs or other digital representations of physical credentials for which Alice doesn’t have proper VCs
- Usernames and passwords
- Personal data of all kinds that Alice uses to create self-issued VCs, fill out web forms, or simply store securely
Many people store these kinds of data in password managers or operating-system-specific tools like Apple’s Keychain. People who hold cryptocurrencies also have one or more cryptowallets to store keys and addresses. These various protowallets suffer from several problems:
- They are often proprietary systems. As such, they suffer from many of the problems that I’ve delineated for administrative identity systems. The most limiting is that they can be used for only the purposes their owners allow.
- While they might be open, allowing other parties to store things in them, the types of use cases are tightly controlled.
- They use inflexible data schemas that limit the kinds of data they can store.
- They aren’t built on open standards and thus lock people into a specific platform. I’d hate to reenter all the login data I have stored in my password manager, for example.
- They lack consistent user experiences. My password manager, keychains, smartphone wallet, and cryptowallets all behave differently. Sometimes even the same tool, like a keychain, differs from platform to platform despite being created by one organization.
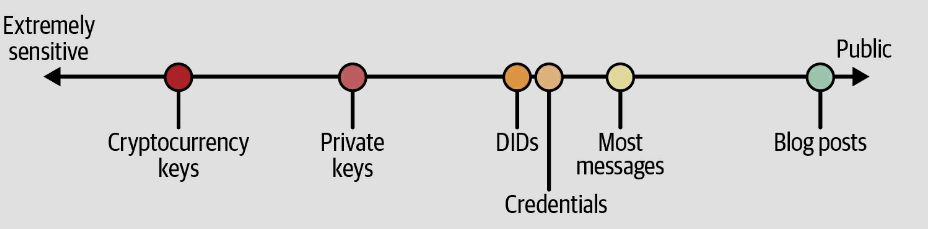
An identity wallet overcomes these problems and has the added advantage of putting all of your important documents and relationships in one consistent place. Thus, many people will opt to move sensitive data from protowallets into identity wallets. Other terms you might hear in the context of identity wallets are personal data store and vault. The variety of information that might be stored in an identity wallet may feel like a loose grab bag of digital stuff. The line between an identity wallet, a personal data store, and a vault is blurry, but they are distinguished by both their sizes and the types of data they contain. A vault might be a secure place to store all my digital stuff, while a personal data store holds all the information I have about me and an identity wallet is just the information I use to recognize, remember, and interact with others. Another key distinction between these three stores is the level of protection they must offer. Figure 1 illustrates the levels of protection we might require for various kinds of personal information.4 Information like my cryptocurrency keys needs much stronger and more robust security protection than the messages I’ve exchanged with Amazon or my friends. Personal data stores and vaults may get by with weaker protections for the data they hold than an identity wallet would. These distinctions provide guidance on the design and implementation of an identity wallet. [1]
Figure 1. Relative protection requirements for personal data
The Roles of Agents
Identity agents are software services that manage all the stuff in the wallet. Agents store, update, retrieve, and delete all the artifacts that a wallet holds. Beyond managing the wallet, agents perform many other important tasks:7
- Sending and receiving messages with other agents
- Requesting that the wallet generate cryptographic key pairs
- Managing encrypted data interactions with the wallet
- Performing cryptographic functions like signing and verifying signatures
- Backing up and retrieving data in the wallet
- Maintaining relationships by communicating with other agents when DID documents are updated
- Routing messages to other agents
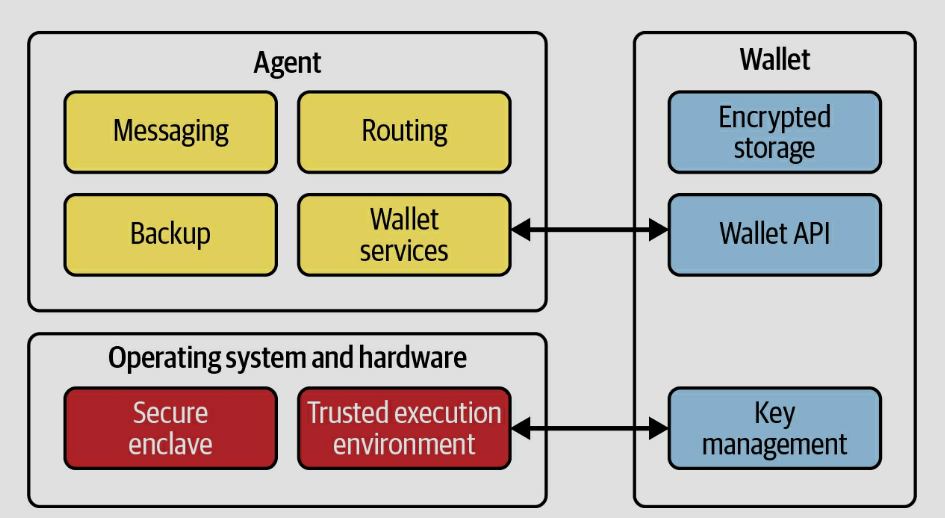
Figure 2 shows the relationship between an agent, a wallet, and an underlying operating system. While most current implementations pair a single agent with a single wallet, the presence of an API means that it’s possible for one agent to use several wallets, or for multiple agents to access one wallet. Some specialized agents might not even need a wallet, such as those that just perform routing, although most will at least need to store their own keys.
The key-management function in the wallet includes events for cryptographic keys like generation, storage, rotation, and deletion. Key management is performed in cooperation with the operating system and underlying hardware. Ideally, the operating system and hardware provide a secure enclave for key storage and a trusted execution environment for performing key-management functions.
Figure 2. The relationship between identity wallets and agents
The basic functions shown in Figure 2 might not seem to have much to do with identity. Identity-related activities like authentication and credential exchange are built on top of these basic functions. The agent can issue, request, and accept VCs. The agent also presents and verifies credentials. Specialized messages perform these activities [2]
Properties of Wallets and Agents
The identity wallets and agents discussed above have several important properties that distinguish them from the protowallets that most people use now:
- Open, substitutable, and portable
The discussion of the properties of email, showed the important features that result when a system is based on a standard set of protocols. Alice should see similar benefits from her identity wallet and agent that she enjoys in email: choice, consistent user experience, and flexibility—all design features of an identity metasystem.
- Secure by design
Security is a nonnegotiable feature for identity wallets and agents. Some security features are the result of mutually authenticating DID exchange as the basis for relationships that natively support confidential messaging. Some security features depend on good engineering of things like the wallet’s encrypted storage or the wallet API. Still others result from governance of the overall ecosystem.
- Private by design
As you know, privacy by design doesn’t layer privacy onto an already built system. Rather, it uses specific design principles to ensure privacy is the default. Identity wallets and agents provide privacy in their design by supporting minimal disclosure of personal data using zero-knowledge proofs (ZKPs) and other techniques, properly encrypting data so that it’s visible only to the intended party, and engineering anticorrelation into the system with techniques like blinded identifiers.
- Autonomous
As key components in algorithmic and autonomic identity system architectures, agents and wallets give people tools for exercising control authority over identifiers and personal data. This control is the basis for autonomy in digital relationships.
- Consistent and familiar in their user experience
There’s a saying in security: “Don’t roll your own crypto.” I think we need a corollary in identity: “Don’t roll your own interface.” By supporting the exchange of data based on VCs, identity wallets and agents provide a single means of accomplishing many tasks. One of the important UX features of identity wallets and agents is that people do not manipulate cryptographic keys and DIDs; rather, they manage relationships and credentials. These are familiar artifacts that people understand. [3]
References
[1] Windley, Phillip J.. Learning Digital Identity (pp. 511-514). O'Reilly Media. Kindle Edition.
[2] Windley, Phillip J.. Learning Digital Identity (pp. 516-518). O'Reilly Media. Kindle Edition.
[3] Windley, Phillip J.. Learning Digital Identity (pp. 519-520). O'Reilly Media. Kindle Edition.
| Children Display |
|---|