...
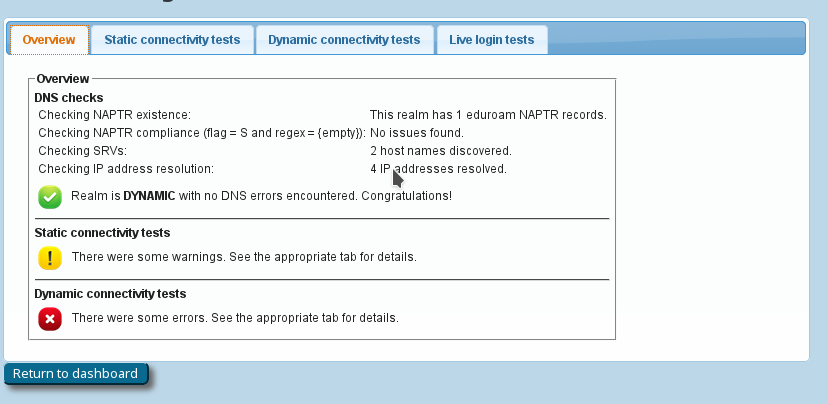
If you have supplied the CAT with the realm which you are using in eduroam, an extra service is enabled for you: the CAT can send live data probes through the eduroam infrastructure to see if your realm's RADIUS server is reachable and whether it passes various sanity checks. All these tests are triggered by pushing the button "Check realm reachability". You will be presented with an overview page immediately while various tests are executed in the background:
The tests will take a few to several tens of seconds, and will give you an in-depth overview of how your RADIUS server is doing in the world of eduroam. The tests include
- a DNS check whether your realm is publishing NAPTR records for eduroam Dynamic Discovery; and if so, whether all DNS records are correct (if you don't know what Dynamic Discovery is, please talk to your national federation operator. It's cool!)
. If the DNS checks were successful, the CAT will make actual use of the discovered RADIUS Dynamic Discovery server targets and try to connect. It will present a mix of valid and invalid certificates and will check whether the server acted correctly on receipt of these certificates. - the results of actual authentication tests which were sent in the moment you pushed the button: these will not log anybody in (we don't have actual user credentials) but even with the planned failed authentication, we can run lots of diagnosis on your server. The web page will let you know if we found some oddities you might want to take care of:
- Authentication round-trip times to your realm which take more than 5 seconds are suspicious
- Your server must be able to send and receive UDP fragments (some firewalls choke on that)
- There are a number of RADIUS attributes that are commonly present in authentication requests; some servers behave strangely on receipt - we'll let you know if yours is problematic
- Checks regarding the structure and validity of your server, intermediate and root CA certificates. These checks are as thorough as checking everything that is described in prose on the EAP Server Considerations page. Here is a typical output if your server certificate is "from the 1990s" (i.e. didn't keep up with all the recommendations and requirements on server certificates in recent years):
- If the DNS checks were successful, the CAT will make actual use of the discovered RADIUS Dynamic Discovery server targets and try to connect. It will present a mix of valid and invalid certificates and will check whether the server acted correctly on receipt of these certificates
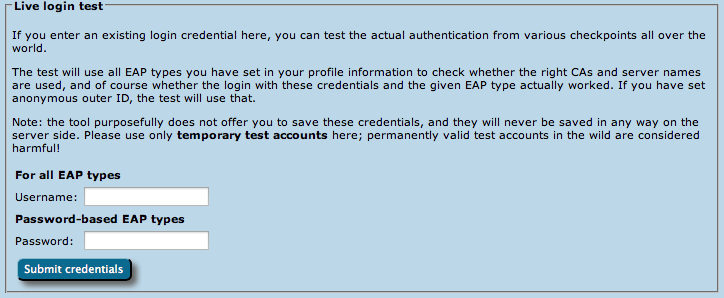
- If If you feel comfortable giving CAT access to short-lived real authentication credentials (for debugging purposes with test user accounts only!), then you can run an actual positive authentication test; in which case we can run even more diagnosis.
Other features
...