- Created by Susanne Nägele-Jackson, last updated on Sep 03, 2025 5 minute read
This section presents the development history and first practical implementations of the QKD scheme and equipment. These include first theoretical work and developed protocols by Bennett and Brassard. The systems were continuously improved together with overall optical technologies development. These were laboratory implementations, only in recent years commercial vendors started to provide commercial, operational grade solutions.
BB84
In 1984 Bennett and Brassard [BEN2014] proposed a concept of Quantum Cryptography (or Quantum Key Distribution, QKD) where a secret and shared key is created between two parties “Alice” and “Bob”. It guarantees that no eavesdropper “Eve" can obtain information regarding the key, and that there is no way to decrypt the communication between Alice and Bob that is sent via a public, assumed unsecure channel. Figure B.1presents the BB84 protocol by Bennet and Brassard (using horizontal, vertical, -45 degrees and +45 degrees polarisations. This concept of the communication protocol relies on four different non-orthogonal quantum states (e.g. different polarisations of a photon) transmitted through a quantum channel to carry Alice's random key. In the example above, Alice assumes the use of the horizontal and the +45 degree polarisations for encoding the “0" and the vertical and -45 degree polarisations to encode the “1". It is important to record every polarisation decision from Alice when a quantum bit is sent over.
At the same time, if Bob randomly uses either a polariser for diagonal polarisations or an alternative polariser that works in the horizontal/vertical direction (it is important for Bob to keep in memory every choice made and the state of polarisation that he measures) then, looking at the result, one sees that the probability of a random result is 50%, as it is the probability of using the wrong analyser. After exchange and transmission of photons with at least twice the number of bits as the final key, Bob discloses to Alice using the public channel the series of analysers that were used by him (however, without its results). In the next step, Alice performs a comparison of Bob's received sequence and returns information regarding the mapping between bits and photons that were sent by Alice. In this way, the shared key is composed of only compatible bits.
Ekert's solution based on Einstein-Podolsky-Rosen (EPR) pairs of particles
The BB84 protocol has been widely described and discussed but other protocols have also been developed. An example is a solution proposed by Ekert [EKE1991]. It relies on quantum correlations between Einstein-Podolsky-Rosen (EPR) pairs of particles. In this approach, the spin of one of the EPR pairs is measured and it is performed randomly and independently by each end. In the end, it is verified if the same detector basis was used. If the basis was indeed the same, results will be opposite due to the complete anticorrelation of the EPR particles. As a result, shared keys can be established in a similar way as in the BB84 protocol. In this approach, it is not required to generate random numbers so it does not impact security in this area. Results of the measurements are not determined prior to the measurement itself. If one considers in this case an eavesdropper that would perform measurements, it will result in the increase of the error rate of the exchanged key. Ekert’s approach has the advantage that using EPR pairs is the certainty of exactly one particle arriving at each end of detectors.
B92
In 1992, Bennett published a minimal QKD system - B92 [BEN1992]. It uses two non-orthogonal states to establish a secure connection between transmission ends. In this approach, Alice again sends a random and recorded sequence of quantum states corresponding to bits “0” and “1” to Bob where he measures each state he receives with either one of the projection operators that correspond to randomly recorded bits. In such a case, a pass state will be noted only in 50% of the bits that are inline and common between Alice and Bob. When the bits are different, a pass state will never be recorded. After exchanging at least four times the number of bits (the required length of the final key), Bob discloses over the public channel to Alice the accepted bits passed during measurements. In this way, the final key elements are derived. Looking at the protocol implementation, one can use normally polarised photons or photons with different phases.
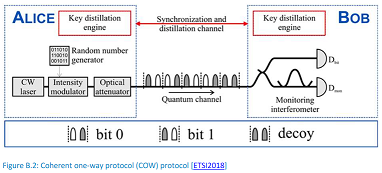
Coherent One-Way Protocol
Coherent one-way protocol (COW) [COW2012] is the quantum key exchange protocol mainly used in the new generation of IDQuantique devices [IDQD2020]. The COW protocol is a distributed-phase-reference protocol (like differential phase shifting - DPS), which relies on the coherence between successive non-empty pulses to ensure the protocol security. In the COW, QKD protocol logical bits are encoded in time. The encoding is provided by an intensity modulator, which generates weak pulses in specific time-bins. Each bit is encoded by sending a weak coherent pulse in one out of two possible time-bins (with the probability 50:50), while the other time-bin remains empty. These states can be discriminated by a simple time-of-arrival measurement on each state. In addition, a third state called a decoy sequence with both time-bins containing weak coherent pulses is randomly prepared.
References:
[BEN1992] Charles H. Bennett, Gilles Brassard, N. David Mermin, Quantum cryptography without Bell’s theorem, Phys. Rev. Lett. 68, 557 –Published 3 February 1992, https://journals.aps.org/prl/abstract/10.1103/PhysRevLett.68.557
[BEN2014] Bennett, Charles H., Brassard, Gilles, "Quantum cryptography: Public key distribution and coin tossing". Theoretical Computer Science. Theoretical Aspects of Quantum Cryptography –celebrating30 years of BB84. 560, Part 1: 7–11. doi:10.1016/j.tcs.2014.05.025, https://core.ac.uk/download/pdf/82447194.pdf
[COW2012] Khaleel, A. I. (2012). Coherent one-way protocol: Design and simulation. 2012 International Conference on Future Communication Networks. doi:10.1109/icfcn.2012.6206863
[COW2019] Da Lio, B., Bacco, D., Cozzolino, D., Ding, Y., Dalgaard, K., Rottwitt, K., & Oxenløwe, L. K. (2019). Experimental demonstration of the DPTS QKD protocol over a 170 km fiber link. Applied Physics Letters, 114(1) doi:10.1063/1.5049659
[EKE1991] Ekert, Artur K., "Quantum cryptography based on Bell's theorem". Physical Review Letters. 67 (6): 661–663. Bibcode:1991PhRvL..67..661E. doi:10.1103/PhysRevLett.67.661. PMID 10044956. S2CID 27683254
[ETSI2018] ETSI GR QKD 003 V2.1.1 https://www.etsi.org/deliver/etsi_gr/QKD/001_099/003/02.01.01_60/gr_QKD003v020101p.pdf
[IDQD2020] https://www.idquantique.com/quantum-safe-security/products/
[ZBI1998] H. Zbinden, H. Bechmann-Pasquinucci, N. Gisin, and G. Ribordy, Appl. Phys. B67, 743 (1998)
- No labels