This page defines a reference design for a platform that can be used to provide an IdP as a Service offering that covers the needs of Research & Education (R&E) institutions.
Specification
This section defines the minimum requirements to be implemented by an IdP as a Service (IdPaaS) offering.
Platform requirements
The following requirement apply to the software used to create and manage an IdP.
| Requirement | A1 |
| Title | Handle SAML authentication |
| Description | IdP MUST be able to handle SAML2 authentication |
| Configurable | No |
IdP requirements
The following requirements apply to the hosted IdP itself.
Authentication
This category defines requirements for the authentication performed by the IdP.
[AU1] Handle SAML authentication
The IdP MUST be able to handle SAML2 authentication
[AU2] Common standards
IdP MUST adhere to saml2int, and relevant eduGAIN profiles
[AU3] No SAML1
IdP MUST NOT be able to handle SAML1 authentication
[AU4] Identifier support
The IdP MUST support the following identifier types:
- persistent nameid
- transient nameid
- ePPN
- ePTID
- subject ID
[AU5] eduPerson support
The IdP MUST support the following eduPerson attributes:
- DisplayName
- CN
- SN
- Name
- edupersonScopedAffiliation
- edupersonEntitlement
[AU6] SCHAC support
Support is needed for at least the following SCHAC attributes:
- schacHomeOrganisation
[AU7] eduMember support
The IdP MUST support the following eduMember attributes:
- IsMemberOf
[AU8] Force Authn
The IdP must support SAML Force authentication
[AU9] SSO session time
The IdP must support SSO, session time must be configurable
[A10] Authentication Context
The IdP MUST support providing LoA information through Authentication Class Context ref
Credential Handling
[CH1]
Attribute release
[AR1]
User management
[UM1]
Metadata consumption
[MC1]
Logging
[LO1]
Statistics
[ST1]
Security
[SE1]
Branding and contact data
[BC1]
Architecture
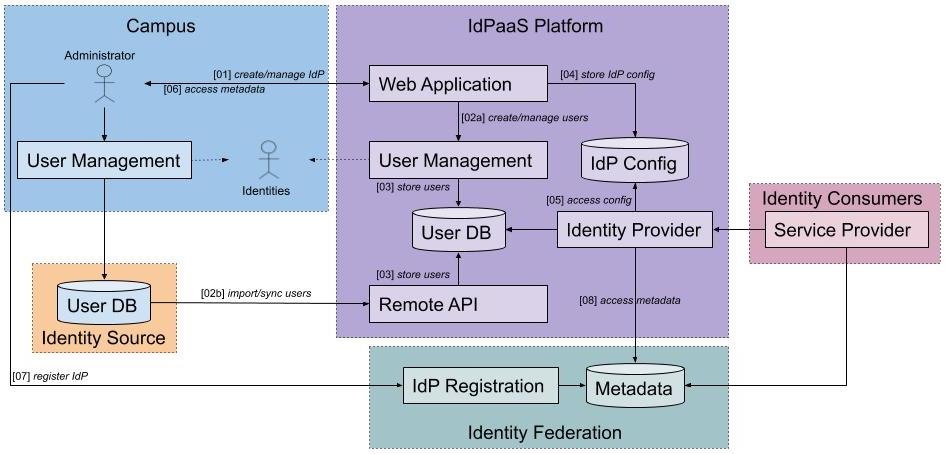
This section describes one possible architecture of an IdPaaS platform to support the R&E specification.
Components
- Web Application
- User Management
- User DB
- Remote API
- IdP Config
- Identity Provider
Flow
- Create/manage IdP
- User Management
There are two ways provided to manage user identities, either using the platform internal user management or using an existing user database. Both options must be supported by the platform, but use may be limited to one option at a time.- Create/manage users
The platform offers an integrated user management to create and manage identities locally using the web interface. - Import/sync users
An alternative to the integrated user management is using an already existing user database. The platform offers an API that allows the import or synchronization of user identities from a remote user database into the internal database.
- Create/manage users
- Store users
User identities are stored in the internal database, regardless whether they were added via the web interface or API. - Store IdP config
The configuration of an IdP created with the web application is stored within the platform. - Access IdP config
The IdP software uses the stored configuration to spawn an IdP service. - Access IdP metadata
The user receives the metadata for the IdP as an XML file. - Register IdP metadata
The metadata is provided manually to the targeted identity federation. - Access metadata
The IdP receives the metadata of the configured federation.
Implementation
https://github.com/sitya/samlidp