Archived
This board has been created in GN5-1 and was archived at the end of the project.
Please visit the new GN5-2 Incubator Dashboard to view all Incubator activities.
Completed activities
Ongoing activities
Pending ideas
TIM students
Active members
Iterations
The GN Trust and Identity Incubator (“T&I Incubator”) aims to develop, foster and mature new ideas in the Trust and Identity space in Research and Education. The incubator will investigate new technologies that currently have no place (yet) in the services ecosystem of the GÉANT project. This may include to test and experiment with potential new features for existing GÉANT services. In addition also business case development for potential new services and developments that would improve data protection and privacy aspects in services or software are in scope.
The T&I incubator runs four to eight incubator activities per project year in parallel. These incubators typically take about 6 months and employ an agile methodology to enable rapid development of ideas. Preferably at least two subject matter experts work together with support from the project team. Subject matter experts are recruited from within the team or, preferred, sponsored by their NRENs. In addition, the project team facilitates the incubator track by providing a scrum master and dedicated developers.
Main Incubator Board (MIB) aims to represent a broad view on Trust and Identity related developments in R&E. MIB members are senior subject matter experts from the European NREN trust and identity community. They evaluate new ideas and provide advice to the work package lead. They are also responsible for reviewing activities at the end of each incubator cycle and providing recommendations on how to proceed. The incubator team presents their results regularly to the the MIB's and the wider community. In the middle and at the end of a cycle there are two events public events, so called sprint demos.
The service task operates and maintains the T&I services in the GÉANT project. The incubator works closely with the responsible service owner on activities that have an impact on an existing service. They are already involved in the selection of new activities to ensure that the topic is appropriately supported. Once the activity is completed, all results are handed over to the service owner, who will take care of further development.
Some of the Incubator's outputs are not handed over to a specific party, but are made available to the wider community. These are, for example, the results of studies and research that are published or software that is publicly released as open source. All results are publicly available and announced via the project's news channels to inform as many community members as possible.
In addition to the general R&E community, the Incubator sometimes works with external partners. These can be other communities, projects or groups that develop software products or provide services. Examples are institutions, individual NRENS or groups such as the Shibboleth Consortium.
The Incubator accepts proposals from the entire R&E community as long as they are suitable to improve the T&I space. All kinds of innovative ideas are welcome, regardless of whether they are about new products, improving existing services or even completely disruptive. The format for submitting a proposal is designed to be as simple as possible. There is a "Call for Ideas" page in the GÉANT wiki where anyone can share their ideas. All you have to do is create a new row in the table and describe your own idea. Other community members can comment and support it. The more popular an idea is, the more likely it is to be implemented in the Incubator. New ideas can be submitted at any time, but there is a deadline before each cycle so that they can be considered for the next cycle.
Call for IdeasActivities
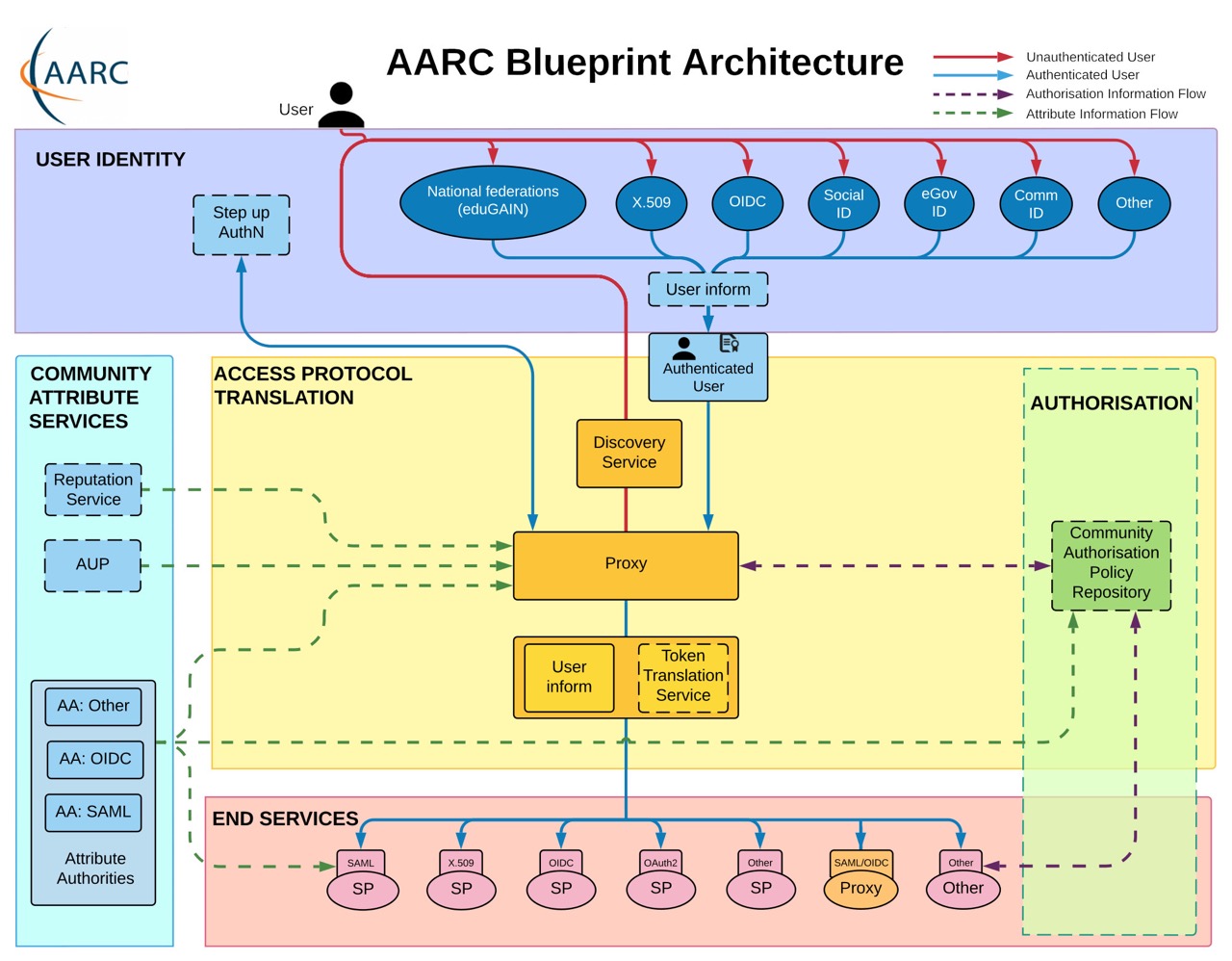
Self-sovereign identity and the AARC BPA
The AARC Blueprint Architecture (BPA) describes a "Community AAI" solution, a set of
software building blocks that can be used to implement federated access management solutions
for (inter)national research collaborations. The benefit of the BPA is that its proxy-based
architecture provides both a technical integration point for authentication and
authorisation, as well as a centralised point for implementing the research communities'
policies. The BPA also identifies a "membership management service" which implements
community-specific onboarding to help establish the researcher's status and may be used to
issue community-specific attributes to establish roles and rights. Implementations of the
BPA, like eduTEAMS and SRAM, have greatly improved the capability to use FIM for research
communities.
At first glance, a SSI based model may offer similar benefits as the AARC BPA model, while
reducing the number of impediments as a wallet model may take away the need to have a proxy
as the central authentication gateway. This activity will further explored the potential use
of SSI technology in the context of the AARC BPA. It will describing where SSI technology
may be leveraged, explore benefits and challenges and describe how that may be implement. A
number of technical pilots will test the assumptions.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
Based on multiple workshops with representatives from the wider community, a report on decentralised identity management was published. It is publicly available to the community

Account Linking
Account linking is, in principle, a simple process of joining users digital identities.
Users have to prove that they own two or more digital identities, which are consecutively
linked together in the identity management system. CESNET has very positive feedback on
ELIXIR workflow for account linking. User signs in with one identity, then with a second
one, and the identities are linked. The positive feedback is coming not only from the ELIXIR
community but also from users from other communities, even outside the life-science area.
The significant issue of the workflow is its user interface, which is still too complicated
for users to navigate through smoothly. Because the process consists of several steps,
skipping one step or leaving the linking process unfinished makes it even more prone to
errors. Users need a straightforward interface that will guide them step-by-step through the
whole process.
The goal of the topic is to develop a new web application for account linking, test it with
end-users and improve it based on user feedback. The application has to support a
recommendation system that tries to guess linkable identities. It also has to deal with all
possible situations in a user-friendly way. The situations include linking identities that
already belong to different registered users or linking identities neither of which belongs
to a registered user.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The source code was submitted upstream to the Perun developers.
Alternative MetaData eXchange
With the growth of the metadata feeds all over the world, together with the increased need
for catering for multiple federations at once, Service Providers are increasingly reliant on
the MetaData Query (MDQ) protocol, for Relying Party metadata lookup. (MDQ is also commonly
referred to as MDX (MetaData eXchange) for historical reasons: the name of a mailing list
where the spec was discussed.) This protocol is however not widely deploy at this time, due
to technical complexity In addition, for MDQ there is only one implementation in common use:
pyFF. This is a risk as it creates a high dependence on that piece of technology.
This activity seeks to simplify the scalable use of MDQ, both for federations that currently
operate a MDQ as well as for federations tat do not provide an MDQ service. In addition it
wants to create an alternative implementation, next to pyFF, for creating and managing XML
metadata. The aim is to deliver EntityDescriptors as flat files in such a way this mimics
MDQ protocol and combine that with Global DNS to create a super fast and highly redundant
distribution mechanism for MDQ.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The design, source code and documentation was be made available to the community

Acceptable Use Policy Service
The primary goal of the Authentication and Authorization Infrastructure (AAI) is to provide
centralized authentication and authorization mechanisms. In an environment based on the AAI,
one of such authorization rules might be fulfilling the policy requirements, set i.e. in an
AUP document defined by the community, service provider, or organizational unit. In general,
when the resource owner or provider decides that a specific policy has to be enforced when
the resource is used, AAI needs to provide a mechanism for both sides to manage and fulfill
this requirement. These rules need to cover several cases, i.e. a situation of actively
using the resource (i.e. web-based service login), as well as just-in-case scenarios, like
the data provisioning.
This topic aims to explore the area of enforcing acceptance of Acceptable Use Policies as an
activity of managing access to resources. We like to understand which parties (e.g. user
communities, e-infrastructures, resource owners, …) need to be involved in the process and
how to combine their requirements together. Based on the analysis we will develop a
web-based application which will provide tools to manage AUPs on a central level (within the
AAI) and let users approve (whilst recording this act) such a policy document.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The source code is publicly available to the community and will be maintained by CESNET. The final product will be tested as a part of the Life Sciences AAI (LS AAI), utilising the Proxy Identity Provider (SaToSa) and the Identity Management System (Perun) as the integration points.

Community Tagging
Research communities have a need to express and potentially share certain trust marks on IdPs and SPs. These trust marks may differ from existing trust marks issued by identity federations. This is why this activity implemented a proof of concept based on a given set of community requirements and investigated in potential scenarios and impacts.
Activity page-
Results & Deliverables
The following results were created and delivered:
- Community Tagging GAP analysis
- Proof of concept using Access Check Tool in conjunction with Jagger
- Video: create a federation and new entity catergory
- Video: Access Check
- Video: Jagger after Access Check
-
Ownership & Utilisation
The work has been concluded. Documentation on the prototype is publicly available and the results were provided to the SIRTFI community to further pursue this POC.

Community-Based Trust
This activity examined how identity vetting and token registration can be scaled for second-factor authentication scenarios where participants are distributed over EU and beyond. As part of this activity a specific flow - based on a community-based approach - was investigated. It takes into account the concept of the Web of Trust. While this mechanism typically does not work well in broad user groups, it is very well suited to distribute trust between small groups where a pre-existing trust fabric is already in place, as we typically have in research communities. What was missing is a means to make this trust network auditable and transparent. In order to make the trust network transparent, this activity identified and developed tools to support this flow.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The outcome is intended to be used in the scope of research communities. In collaboration with the eduTEAMS task the results can be used to provision and improve the Stepup solution of the GÉANT service.

Cryptech HSM
In many of the T&I services in the R&E sector, there is a need to securely store sensitive data like key material. Currently, this is rarely done using Hardware Security Modules (HSM) as they are associated with high costs. The goal of this activity was to evaluate the capability and applicability of affordable devices from the Cryptech project for use cases within the GÉANT project and to set up devices for testing purposes.
Activity page-
Results & Deliverables
The following results were created and delivered:
- Evaluated usage of Diamond Key appliances and capabilities
- Detailed community use-cases for HSM
-
Ownership & Utilisation
The work could not be concluded as Diamondkey seased operations during the evaluation period.

Distributed Identity Revisited
Distributed Identity (DI) presents an interesting paradigm for the T&I NREN community. Its concepts are very appealing and align well with public values in our community. At the same time many of the technical and functional properties are still in development and present numerous questions and challenges, as was shown in recent work in NRENs and in the Incubator. The activity proposed builds on earlier work and investigates the following aspects of DI:
- What roles could/should GEANT and NRENs play in a DI ecosystem, and what are the associated benefits, challenges and risks?
- Which current services in the GEANT portfolio would benefit from the use of DI, and what would that look like?
- To what extent can existing initiatives implementing distributed ledgers technology be used to act as a Verifyable Data Registry to satisfy the above use cases and requirements? We should test with for example EBSI, etherium or Sovrin. How do these compare to the IRMA solution we previously tested. (IRMA does not use DLT).
- Initial testing with IRMA revealed a wallet based approach may not always provide an optimal user experience. What requirements do we have for the User interface (wallet/app) and can we implement or mock these to test these requirements with stakeholders.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The investigation of DI use cases for GÉANT, NRENs and institutions was completed. The results were published as a report.

Discovery Pilot
Discovery is used in Federated Identity Management to locate the users home organization. This activity evaluated the pilot discovery service ran in the previous GÉANT project and investigated if/how the implementation technology Seamless Access developed within the RA1 project can be used for an implementation in eduGAIN.
Activity page-
Results & Deliverables
The following results were created and delivered:
- DSX Discovery Service Feedback Report
- Preparation of handover to eduGAIN service activity
-
Ownership & Utilisation
The work has been concluded in the Incubator and was handed over to the eduGAIN service task for the purpose of making a production service.
Distributed Identity for researchers
A new paradigm, Distributed Identity, tries to let user be in direct control of the profile information they share with services. Rather then letting others provide claims towards a service, the users collects claim themselves from various sources and independently provides these when so requested by services. The services can check the validity of these claims against a central verifiable claims registry. This activity investigates the functional requirements for such a system by interviewing key stakeholders.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
This activity explored the applicability of distributed identity for research use cases. The results were published in a report and made available to the entire community.

SFA - Distributed Vetting
Several research communities, especially in the life sciences domain, have a need to use second factor authentication to improve the quality of their authentication. One of the challenges identified was how to securely vet the second factor tokens of the participants of a collaboration in a case where the members of the collaboration are very distributed, as is the case in most pan-EU research collaborations. This activity investigated, together with research communities, how the token registration can be scaled for scenarios where participants are distributed over the EU and beyond. The aim of this task was to identify ways this vetting can be done.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
A final report was delivered. The activity will continue for another Incubator cycle.

eduGAIN PoC
The eduGAIN service activity will set up a POC in order to evaluate the new OpenID
Federation (OIDfed) standard and wants to eventually create an official eduGAIN Technology
Profile to extend the current service.
The Incubator contributed to the eduGAIN PoC in creating and improving standards and policy
development for eduGAIN and national federations, software development for the eduGAIN PoC,
building a (scalable) resolver which can be deployed by fedops and eduGAIN, improving
visualisation and reporting tooling, as well as Go based OP/RP.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The architecture and source code is publicly available to the community. This will be used as the basis for other activities in the next cycle.

eduLNK
eduLNK aims to provide software and potentially a servcie for a secure, persistent and privacy preserving link shortener for research and education. Link shorteners reduce a lengthy URL on the internet to something short and snappy, and sometimes easy to remember. As such it is a very well used and liked functionality within our community. Many ‘free’ link shorteners exist, however, their free nature comes with a number of challenges, including serving advertisements and data mining the users behaviour and interests. Next to privacy concerns, many free link shorteners have a limited lifetime for the links they present. eduLNK aspires to deliver a product from and for the community which can be trusted and used securely in a privacy preserving way.
Activity page-
Results & Deliverables
The following results were created and delivered:
- eduLNK source code
- eduLNK prototype
- Onboarding documentation
- New Idea Form
- Final presentation
-
Ownership & Utilisation
A prototype of the eduLNK software was created and a public test instance was made available. With the submission of the official new idea form, eduLNK may become a potential new service in the GÉANT project.
Instant User Provisioning
Some systems, like non-web services, cannot be federated easily because they need user accounts to be provisioned before they can login. A prototype of an instant deployment tool called FEUDAL was developed by KIT. It facilitates provisioning of user accounts using virtual organisations (VO). Feudal is based on OIDC: It is an OIDC client, and it simply transports the information of the /userinfo endpoint along. Feudal is based on the concept of VOs (or authorisation Groups), i.e. the end services provide the information which VOs it supports. Feudal web fronted will only display services for provisioning to a given user based on his VO membership.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The aim of this project was to create an easy to use, adoptable software solution to provision server users and provide this tool to the community. The solution is ready to be picked up and further developed and used by KIT. They plan to use this software in two "Helmholtz" projects HDF and HIFIS in Germany for the foreseeable future. Besides this, the solution was adjusted to the needs of eduTEAMS. The solution was provided to the eduTEAMS service task to be integrated into the GÉANT service.

geteduroam Linux client
The geteduroam service provides a novel way for end users to configure eduroam on their
devices. It helps them to get the configuration correct and secure, by combinding federated
web login with the provision of an x.509 client certificate to use for authentication, it
makes deploying eduroam more secure and minimizes the risk of sensitive credentials leaking
due to a mistaken, insecure configuration.
The Incubator implements a Linux client that interfaces with geteduroam and configures and
refreshes the credential. This can be a commandline tool, but other types of interfaces can
also be considered. If a basic client is available for Linux users, this provides instant
value and makes it also easier for the community at large to make more incremental
improvement after it.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
A working version of the geteduroam client for Linux was created and handed over to the edugain and the geteduroam developers for long term maintenance.

Identity Validation Broker
Both research communities as well as institutions have a need for proper proof of the identity of their users. This ranges from cases where e.g. new students living abroad need to be identified as part of the boarding into an institution, to scenarios where access to (medical) data puts regulatory demands on the research community. Identity proofing is however expensive and scales very poorly, especially in cases where the users are (very) distributed. This activity investigates, based on requirements collected from multiple stakeholders, if and in which way this situation may be improved.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
Our findings indicated a strong desire for information about the capabilities of the various document-based identity verification solutions, which would help in defining what the requirements and suitable deployment model for an R&E focused solution could be. In particular we concluded that further work would be needed to reach a definitive conclusion and recommended: Establishment of a platform for information capture and exchange on document-based identity verification solutions Comparative analysis of available commercial solutions should be performed and made available Surveying of the broader R&E community based on the findings so far to see the level of interest and support more generally Constructing a preliminary business case for a community-operated service following the broader survey It is hoped that an interested party or parties can take this work forward, as further work on this topic is currently outside the scope of the Incubator.

IdP as a Service
The former GN4-2 project developed a solution to offer an IdP as a Service solution (IdPaaS) for hosted IdPs. This activity aimed at investigating the business case of this solution and to create a reference design and implementation for an easy to use software solution to enable NRENS to provide an IdPaaS offering.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The work has been concluded within the Incubator. samlidp.io is available as an open source software for the community and may be used by commercial vendors as well.

Metadata push MDQ
Metadata is at the heart of the trust fabric of current R&E Identity Federations. For the trust to properly propagate, this metadata is first collected from and then distributed by the federation towards the federation members. This activity had investigated a new proposal called "push MDQ", which introduces a new, potentially highly scalable way of distributing metadata.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
All changes made to the pyFF software were uploaded to the official software project to be maintained by the IdentityPython group. Furthermore, all results of the push MDQ analysis and the POC were transferred to the eduGAIN service task for further improvement of the GÉANT service.

Porting oidc-agent to Windows
oidc-agent is a command line set of tools that enables the users to manage and obtain (mostly) OIDC tokens on command line. It follows the design of the ssh-agent and, as such, it can be easily integrated in the user's flow. However, current version only covers Linux and MacOS users. This activity would port the oidc-agent to Windows OS. The expected impact is potentially large, since users from many communities that may use this tool (such as HPC, or any community that need constant access to computing and storage resources as part of their work) typically rely on Windows as their main operating system. This activity investigates the best approach to porting the oidc-agent.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The source code was submitted to the upstream repository and is publicly available to the community. The Karlsruhe Institute of Technology (KIT) will maintain the software.

OIDCfed support on SimpleSAMLphp
OpenID Connect Federation will provide the basis for multilateral connections between RPs
and OPs in a scalable way. Adding OIDCfed support to Shibboleth will already been taken care
of with support also from non-R&E companies, but many of the AAI proxies for research in the
AARC BPA, and at research institutions, are running SimpleSAMLphp as the basis for their
proxy.
The Incubator is in an excellent position to add native OIDCfed support, with support for
hierarchical trust path construction and the ability for policy filtering, to SSPHP, based
on the previous success of its OIDC OP project.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The architecture and source code is publicly available to the community. This will be used as the basis for other activities in the next cycle.

SimpleSAMLphp OIDC OP
SimpleSAMLphp (SSP) is a commonly used software product for both SP and IdP deployments in
Research and Education. In addition it may also be deployed as a proxy. Next to SAML,
various other authentication protocols are supported.While SSP already supports the OpenID
Connect (OIDC) Relaying Party (RP) interface, an OIDC OpenID Provider (OP) implementation is
missing.
This activity seeks to implement an OIDC OP in accordance with the OIDC specification into
SSP. There is an existing module available at Github. It needs to be investigated whether
this is suitable for this activity.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The work has been concluded and the results were provided to the SimpleSAMLphp developers. The source code is publicly available and will be maintained by the upstream maintainers.

Implement OpenID Federation into SimpleSAMLphp and Shibboleth IdP
Related to the eduGAIN OpenID Federation Pilot, we would like to add OpenID Federation capabiliteis to commonly used software in our ecosystem. This activity will complete the work on implementing OpenID Federation into SimpleSAMLphp, as well as start with an implementation for Shibboleth IdP.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The results are be maintained by the Shibboleth Consortium and the SimpleSAMLphp Development Group.

ORCID as IdP of last resort
Many research collaborations as well as campus services need a solution to deal with guest identity, as in many cases not all users are members of the academic Identity Federations. As a result, several federation operators as well as research collaborations operate IdPs or proxies to allow users to authenticate through external identity providers like social ones. This has led to serious reinventing of the wheel. This pilot aimed to bring the widely used ORCID service into the GÉANT IDhub as Identity Provider of last resort. Furthermore organisational and legal aspects as well as technical improvements were investigated.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The work has been concluded with the results handed over to be further developed in the IDhub to improve the GÉANT service.

Passkey passwordless authentication
Passkey promises a new way for passwordless login. The login however does not contain an attestation. How does this new protocol work, how does it integrate into our current ecosystem and how would this work in combination with new paradigms like wallets? The project aims to investigate passwordless authentication in the context of identity federations. This new approach will provide valuable insights into the feasibility and potential benefits of Passkeys as a first factor or even an MFA alternative.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
A white paper about the opportunites of Passkeys in R&E was published.

pyFF Optimizations
pyFF is an open source and widely used product which is used to provide Discovery and
Metadata Query services for identity federation. This topic investigates optimizations in
pyFF operations, including but not limited to, performance and memory consumption. When
processing the eduGAIN metadata, pyFF memory usage balloons to the gigabytes, hereby
inflicting some extra cost when running on procured VM's like AWS. The startup/restart
process speed, and service behavior while being started/restarted may also be improved. In
particular, the service should never throw 5xx errors while in a normal startup/shutdown
process.
The goal of this project is to optimize pyFF memory consumption and (re-)start
behavior.
-
Results & Deliverables
The following results were created and delivered:
- pyFF test report
- Metadata mockup report
- Blog post
- Final presentation
-
Ownership & Utilisation
The aim of this activity was to investigate whether the existing pyFF software can be optimised to reduce memory consumption and improve performance. For this purpose, intensive profiling of the software was carried out and a large number of experiments were conducted. All tests and results were documented in a report, which was passed on to the developer communities of the tools.

eduGAIN Service Catalogue
The eduGAIN Support Team, Secretariat and business development received several requests
from SPs, IdPs and NRENs for an eduGAIN Service Catalogue. Currently the eduGAIN Entities
Database tool and REFEDS Metadata Explorer Tool (MET) are the two services closest to a
service catalogue, but there are inconsistencies between the two tools.
The Incubator attempts to improve the solution based on the outcome of this pilot phase.
Depending on the requirements and use cases that need to be supported, new features can be
added in following an iterative process. If there are not enough participants to provide a
meaningful amount of data, no additional developments will be carried out by the Incubator.
In this case, the software is decommissioned at the end of the pilot phase and the project
is terminated.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The project has reached a point where engagement from the community is required to take the work forward. At this time we have received no offers of engagement and we are therefore stopping our work, leaving documentation and existing code available to any group who may wish to continue developing the Service Catalogue.

Service Status Reporting
The T&I activities of the GEANT project run a multitude of services ranging for eduroam and eduGAIN to InAcademia, eduTEAMS and various smaller helper services for eduGAIN without a single overview of the state of all these services. The highly distributed nature limits our ability to present in a consistent way the status of these services and it hinders us in explaining issues when something is wrong. This is relevant both for members of the GEANT community as well as other other stakeholders like service owners and funding agencies. This activity wanted to create a comprehensive, high level and user friendly publicly facing service dashboard for T&I services. Since many freely or commercially available services for measuring availability already exist this activity investigated and compared them to choose a suitable solution for the GÉANT project.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The result of the market analysis was provided to the T&I service task.

Shibboleth OIDC Extension
Up to now, R&E federations are predominantly relying on the SAML2 protocol. With upcoming needs from industry and commercial service providers the OpenID Connect (OIDC) protocol is increasingly moving into focus. This activity supported the development of an Shibboleth OIDC Extension to the Shibboleth IdP and was paving the way to make the extension a fully sustained product.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The work has been concluded and the results were handed over to the Shibboleth consortium. The Extension is certified by the OIDC Foundation.

Scalable testing for insecure SAML signature validation
The SAML 2.0 protocol relies on XML signatures as the foundation of its security. It is
notoriously complex and allows for many ways to create one or more signatures for any
document, which means an implementation can easily fall victim to accepting not properly
signed data. Even common R&E implementations like Shibboleth and SimpleSAMLphp have had
issues here in the past. Besides these common products, which at least are periodically
audited for such problems, a much larger risk is custom implementations that use different
or even home grown libraries.
The goal of the activity is to deliver a (software or service) solution that assists
identity federation operators in testing at scale of several core security aspects of SAML
service providers within their federation. This topic includes the technical implementation
of the use cases to test against. In addition it designs a concept to support operators to
deploy the testsuite both technically and operationally.
-
Results & Deliverables
This acticity is still in progress
-
Ownership & Utilisation
This activity is still in progress

IdP/SP software testbed
It is currently very hard to test new releases of IdP and SP software against other IdP/SP products. This activity attempts to design an automated test environment. A suitable architecture for an IdP/SP continuous integration platform is to be created. This involves creating use cases and identifying technologies that support them. An iterative approach, in which use cases are successively implemented and products are integrated one after another, is intended to quickly create a functional platform. If the CI approach is successful, ready-to-use software packages can be provided using container technologies such as Docker, to deploy the entire software locally by NRENs or other parties.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
A prototype of an IdP/SP software testbed was successfully created. The results were presented to the community and made publicly available. No group was identified to continue the development of this project.

Automation of SP deployment
While supporting new federations in setting up their infrastructures, there is not much
automation in place. All is done, still very manually, and takes much time. Talking
specifically of the SPs, both for the installation and configuration of the services
themselves, and the required operations to federate them, in order to be able to provide
them in a federated (e.g.eduGAIN) fashion, pretty much all is still left to manual setup. It
would be useful to (new) federations being able to deploy an initial set of services, the
ones which could de-facto start to attract users towards the newly deployed federation
infrastructure and the federated IdPs.
This activity investigates a proxy approach to aggregate the services and potentially
simplify the deployment and integration of tools. The Incubator will make an inventory of
relevant services and discuss integration scenarios with stakeholders. The goal is to create
proof of concept of at least one scenario and present it to federation operators.
-
Results & Deliverables
This acticity is still in progress
-
Ownership & Utilisation
This activity is still in progress

SSH in a Federated World
To allow easy access to SSH based services DeiC has made a SSH Certificate Authority proof-of-concept that issues short-lived SSH certificates based on a federated login. The system requires no specific client - or service side installed programs and makes it possible for the user to use all standard ssh services - as long at the certificate is valid. Depending on the configuration of the participating services the CA allows the user to use the same username/uid across all services. Optionally it can be combined with systemd-userdb services to allow for fully automated user management. The CA can also optionally issue host certificates so the users do not have to trust the servers on first use (TOFU). Initial goal of the activity is to hold a workshop to gather requirements and showcase and discuss existing solutions.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The information gathered was compiled into a white paper, which was shared with the community as an opportunity for further collaboration. A user group is to be established to deal with this subject long-term.

Status Reporting & Notification
To make the global eduGAIN interfederation scalable and interoperable, it is paramount participants adhere to agreed upon standards and community best practices. There are currently already several tools that examine the quality of federation metadata, the connection status of their IdPs and the attribute release status of their IdPs. This activity is about creating a tool to aggregate information from various sources and presenting this in an attractive, easy to understand way to put this information readily into the hands of the federation operators.
Activity page-
Results & Deliverables
The following results were created and delivered:
- Source Code (closed source)
- User documentation
- Live test environment
- Final presentation
-
Ownership & Utilisation
A prototype was developed that meets the expectations of the stakeholders. The tool, in future called "eduGAIN Reporting", was handed over to the eduGAIN Task. In order to develop this further, an eduGAIN reporting development team was founded. The created prototype is used for additional tests with the users and replaced by a productive system a few months later.

Test IdP
This activity creates a freely available, realistic test IdP for the GÉANT community. Based on the needs of the GÉANT community, the solution may offer SAML, OIDC and supports all the latest best practices. The requirements and use cases for such a service will be defined in collaboration with a group of community representatives. Potential features of such a tool are: test for a specific set of attributes, create an account to save a test profile, an open (REST) API to configure the IdP using a (web) client. There are different potential business cases for deployment: as part of the eduGAIN support tools, by GÉANT operations or NREN hosted.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
A Test IdP based on the SimpleSAMLphp software was created. It supports the following tests: R&S Entity category tests, Behavioural tests, Generic attribute profile tests, Refeds Assurance Framework tests, Error scenario tests and Experimental profile tests. The Test IdP was made available in GÉANT Gitlab.

TI-wizard
Magaging the relations between services and identity providers is a challange,
both for emerging adopters of federation technologies, collaborative organisations and institutions alike.
Typically technical complexity and a steep learning curve are the liming factors in the ability
to manage a SAML or OIDC based ecosystem.
A GUI may help reduce the complexity of managing the environment,
as it provides a single integration and organisational interface for managing the relations.
Even so, current proxy products are still rather technically inclined and do not provide
easy to use interface to configure the entities.
This activity takes inspiration from the prototype build in the TIM programme in the previous cycle
and aims to create a (browser based) GUI to allow (proxy) operators to easily configure the proxy.
The GUI is to be build in such a way it may be deployed independently from the product.
A reference implmentation will then be build for both SimpleSAMLphp and SaToSa.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The architecture is publicly available to the community.

Trust fabric for wallets
Europe is working towards a wallet-based identity ecosystem. The
Architecture and Reference Framework
(ARF) is intended to serve as a basis for the implementation of the proposal for the
European Digital Identity Framework. The current version of the ARF has declared the organizational trust out of scope. The
OIDC federation specification seems to have many characteristics that would allow such a
wallet ecosystem to be defined.
The goal of this activity is to investigate and test the use of the OIDC federation protocol
as a trust fabric for a wallet ecosystem. This activity will evaluate ARF for trust
framework related requirements and describe how OIDC federation may be leveraged in with
OpenID4VC The goal is to plan and build a test setup to verify the usability of OIDC
federation in the context of a wallet ecosystem.
-
Results & Deliverables
This acticity is still in progress
-
Ownership & Utilisation
This activity is still in progress

IdP User Profile
Currently, there is no way for federated users to know at which service providers their
account was used to login. This activity developes a mechanism to track federated signing in
events. That would allow an user to check the recent activity on his account in regards of
authentication. Users could see the list if authentications containing datetime, ip and
relying party etc. That would help them to spot suspicious activity.
A user profile page deployed as part of Shibboleth IdP and SimpleSAMLphp would enable end
users to gain insight into where their personal data is used and when it was last released
to various services, as far as the IdP is aware. This feature should only release
information to appropriate user (so after login). It needs to be considered how storing user
data to facilitate this plugin would impact data retention policy of the IdP.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The prototype was presented at multiple events to interested parties. It will be provided to the SimpleSAMLphp/Shibboleth developers after further improvement.

Verifiable Credentials Schema for eduPerson, SCHAC and voPerson
W3C Verifiable Credentials (VC) are increasingly important to our community with the rise of
Decentralized Identity and Wallet ecosystems. Several VC based credential definitions already
exist for expressing skills and micro-credentials, like e.g. the Openbadges 3.0 specification.
However, there is no consistent and community driven definition for expressing the 'identity related'
credentials of the commonly used schema managed by REFEDs like e.g. eduPerson, SCHAC and voPerson.
The REFEDS schema board is setting up a subcomittee to define the VC representations of these
well known credentials so they may be used in an standardized and interoperable way.
-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The documentation is publicly available to the community.

WebauthN
WebAuthn (Web Authentication), part of the FIDO2 Project, is a web standard published by the W3C that enables strong authentication with public-key cryptography, passwordless authentication, and secure two-factor authentication. The standard defines a JavaScript API which allows token registration and subsequent authentication. This activity implemented this API for the open source software SimpleSAMLphp and SATOSA, which enables them to provide 2FA functions to the benefit of the R&E community.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The developed modules were submitted to the upstream repositories to be officially maintained by the simplesamlphp groups and CESNET. The software was provided to the eduTEAMS service task to include it into the GÉANT service.

Webwallet for research use case
The current ARF framework assumes all interactions will be handled via an app on a mobile
phone. While this may suffice for many users, it will leave out groups that cannot or will
not use such devices. In addition, it creates a dependency on the vendors of the devices and
the software they run on. Finally, users may not be willing to store and aggregate work
related data on a personal device.
This activity will investigate if a browser based wallet may be created which can support
(parts of) the ARF. A first version of such a web wallet has been developed as part of the
eDiplomas wwWallet Ecosystem activity.
To confirm usability for our community, the browser based wallet should be tested with the
same scenarios as were previously tested in the incubator using mobile based wallets. The
goal is to describe scenarios, set up a test environment and release at least one new
version of the existing wwWallet.
-
Results & Deliverables
This acticity is still in progress
-
Ownership & Utilisation
This activity is still in progress

(De)provisioning connector for Windows
Identity provisioning and deprovisioning are a necessity for building modern authentication and authorization infrastructures. They are straightforward yet technically complicated part of identity and access management. The basic idea is to deliver identity and authorization information to the managed services, which is complicated by a lack of applicable standards in this area. Therefore, most of the Identity and access management solutions rely on a custom solution for provisioning. To overcome this obstacle, this project extends existing IAM capabilities by implementing a connector to easily provision data to services hosted on Windows OS based on SSH.
Activity page-
Results & Deliverables
The following results were created and delivered:
-
Ownership & Utilisation
The aim of this project was to create an easy to use, adoptable software solution to provision server users and provide this tool to the community As part of a case study the solution was implemented for a Czech University (Faculty of informatics MU) which will continue to use the solution afterwards. CESNET will continue to use and maintain the software for the foreseeable future. Besides this, the solution shall be adjusted to the needs of eduTEAMS. The solution will be provided to the eduTEAMS service task to be integrated into the GÉANT service.
1 Comment
Michiel Schok
Michael Schmidt The "SSH in a federated world" Activity Page links to this page , but confluence says that is deleted. Looking elsewhere, I can find another page where I think this content lives. Could you please check?