Requirement
|
Overview
Several choices were possible, we finally ended up in following the KISS method. The Operating system requirements are:
- requirement #0: LTS operating system
- requirement #1: Benefit from LTS security patches
- requirement #2: Must be able to run DPDK
- requirement #3: (personal requirement) Must be familiar to me
- requirement #4: Able to run Java software as freeRouter is written in Java
- requirement #5: Small operating system software footprint
- requirement #6: Support for IPv4/IPv6
The hardest path would be:
- Create a custom linux distribution using the Yocto project:
The objective is to have tight control of the software installed on the appliance. This guarantees the smallest footprint we hope to obtain. For those familiar with OpenWRT, we can reach a tiny image size. My OpenWRT image is 5Mb.
- Use of NixOS or Nix package manager
This provides an incredible feature: commit/rollback functionality at the package management level!
Note
The features above are still under study into RARE group. We will introduce these technologies once we feel more confident on how to integrate these technologies into a streamlined deployment process.
Article objective
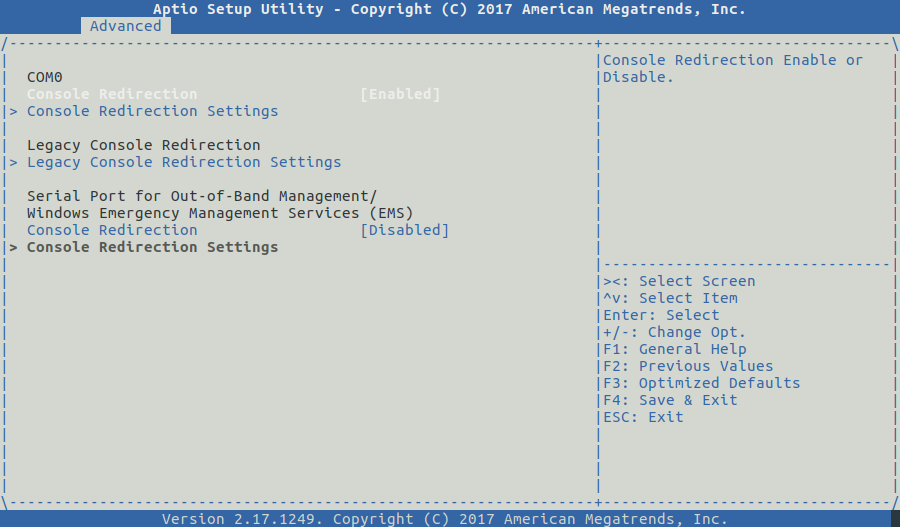
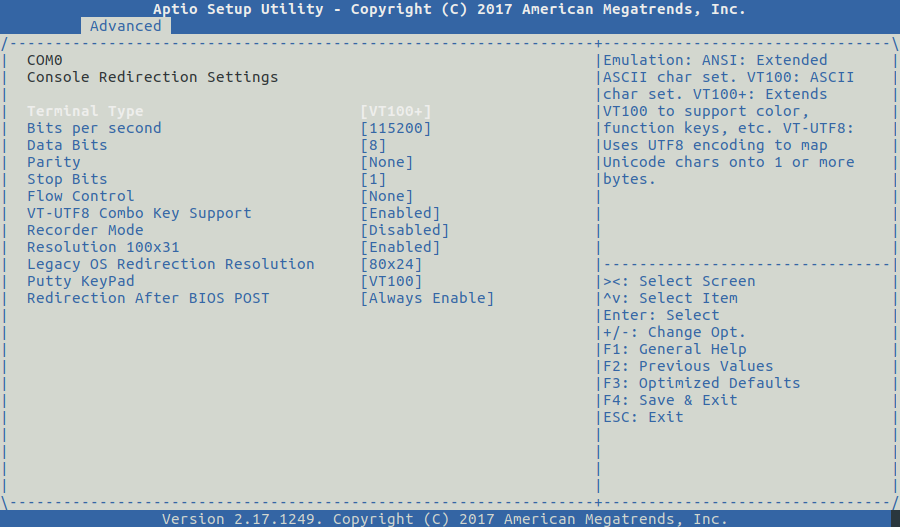
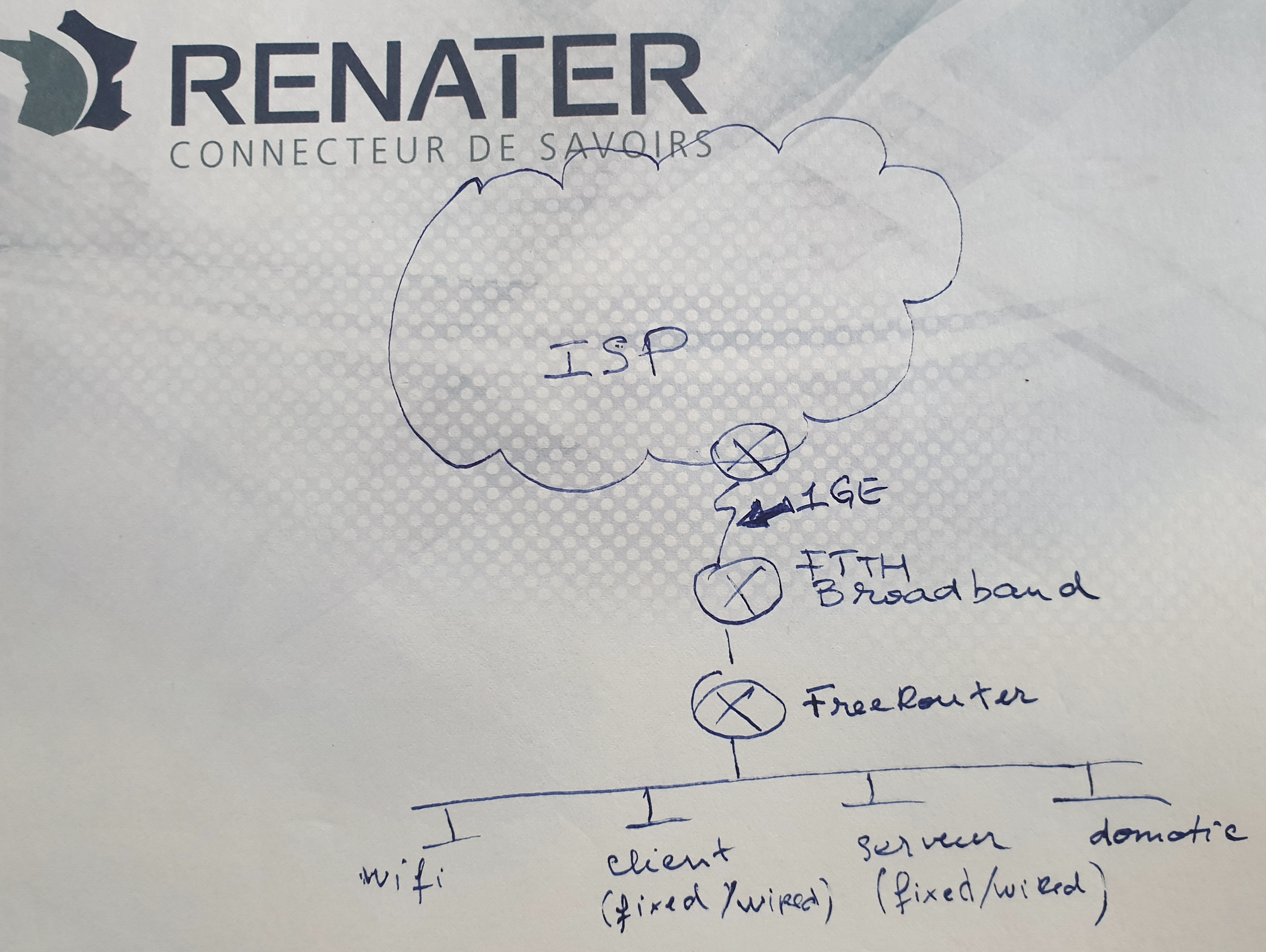
In this article we will go through the major steps in deploying Debian 10 stable aka Buster in order to prepare freeRouter installation.
Diagrams
[ #002 ] - Cookbook
Discussion
Conclusion
In this article, we got our hands dirty and manually installed freeRouter with DPDK dataplane from a clean slate environment. This is done on purpose, as I'd like you to understand the whole installation process in detail. There is an automated installation alternative that will install freeRouter also. However this is will install freeRouter with software backend. If your hardware CPU+NIC is compatible you can just replace the software backend by DPDK backend. At that precise point we have a vanilla genuine installation of freeRouter with DPDK dataplane on an appliance that can survive physical wild environment and power cut. We have just now to create the 2 freeRouter configuration files:
ls -l rtr-* -rw-r--r-- 1 root root 646 Jul 31 17:03 rtr-hw.txt -rw-r--r-- 1 root root 9027 Aug 25 10:02 rtr-sw.txt
RARE validated design: [ SOHO #002 ] - key take-away
- freeRouter installation is not complex. It just boils down to installing a basic supported Linux OS, install Java, some 3rd party software and the freeRouter jar and binaries itself
- In the binary list you'll have a special one called p4dpdk that corresponds to freeRouter DPDK dataplane that emulate RARE P4 program on BMv2 (It does not emulate BMv2 !)
- Though this installation is manual for pedagogic purpose, the installation can be fully automated, just fire up a VM with a bunch of interfaces and test it !
- The installation proposed is highly resilient and will ease upgrade of the appliance (we will see in subsequent article what it means
)
In the next article, we will configure the freeRouter appliance, start the router, and provide configuration in order to have effective basic ping reachability to the FTTH BROADBAND internal IP.
Requirement
|
Overview
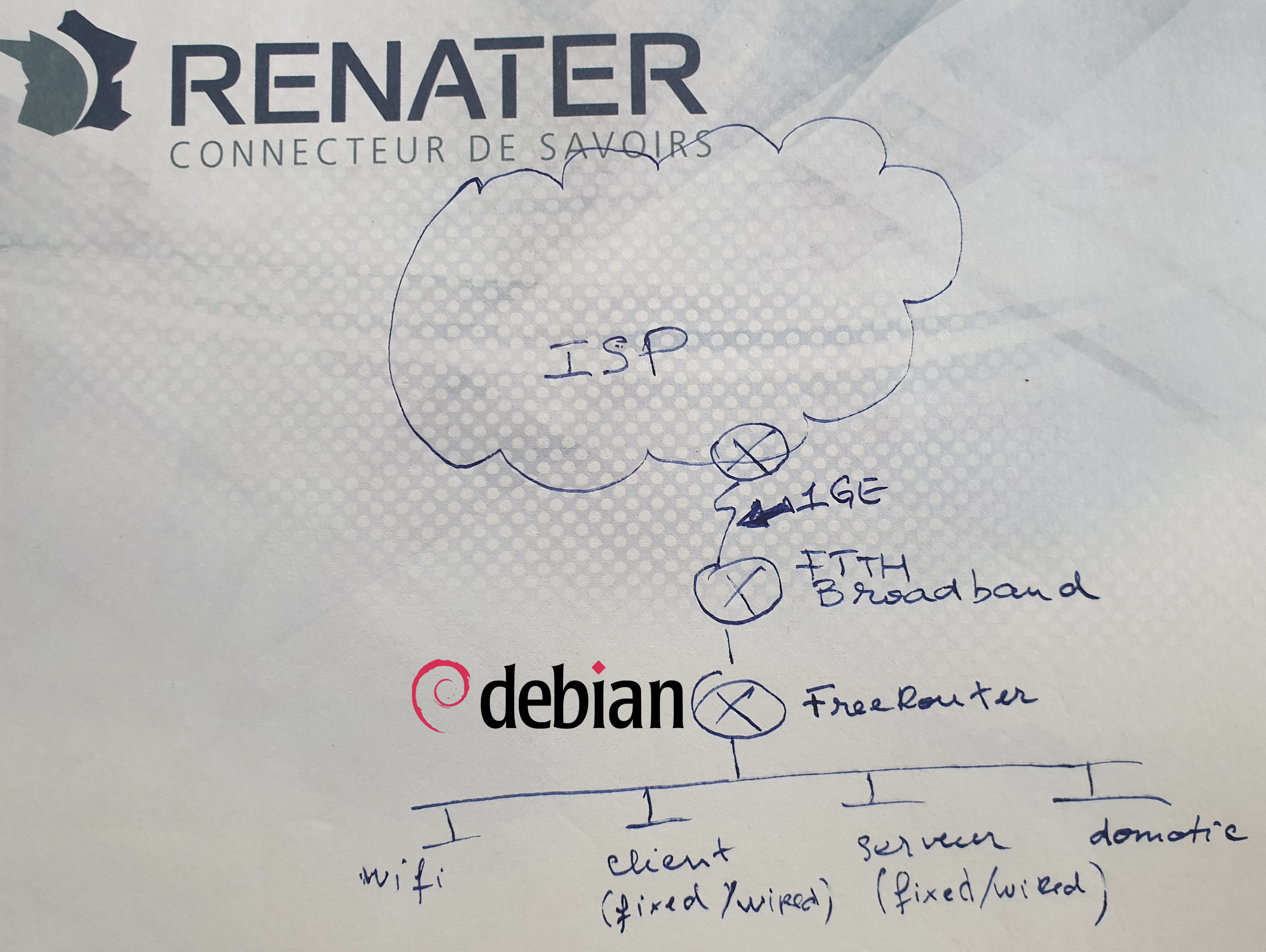
Back in 2004, I deployed a 8Mbps ATM circuit that connected an airline company hub site. Traffic growth increased amazingly since then! In 2020, what does SOHO (Small Office, Home Office) mean nowadays? In our use case we will consider a SOHO connected at 1GE link. This is for example:
- Primary schools, Secondary schools
- Small R&E institution spoke sites
- Home office (especially considering the COVID context)
- Small company spoke agencies
Article objective
In this article we will describe how to build a carrier grade SOHO router (aka CPE) from an actual real platform. In this example let me share with you my personal story and introduce you my SOHO hardware that I'm using at home. It is compliant with the requirements implied by the use cases listed above:
Requirements
- requirement #0: n×1GE capable, ISP uplink is 1GE
- requirement #1: completely silent, the box can be moved to crowded room
- requirement #2: small power consumption, as it is meant to run 24x7. (I'm paying the bill !
)
- requirement #3: Run 64-bit linux
- requirement #4: native support of DPDK
Diagrams
[ #001 ] - Cookbook
Discussion
Conclusion
In this 1st article you:
- had a brief description hardware platform suitable for SOHO
- had a description of the SOHO use case in 2020
- get a rationale on why this platform has been chosen
- had a brief description of the selected Operating System
- get a rationale on why this OS has been chosen
RARE validated design: [ SOHO #001 ] - key take-away
- RARE/FreeRouter is a strong candidate for SOHO with multiple dataplane support solution.
If you are a company you run RARE/freeRouter with a versatile P4 switch such as APS Networks® BF2556X-1T or WEDGE, but as a SOHO with a small budget you can run it with a DPDK dataplane and for older hardware you still have the possibility run it with a pure software dataplane
- RARE/freeRouter is the first element at the very edge of the MPLS seamless architecture
End to end MPLS is now possible for the Service provider at an affordable price
- RARE/freeRouter design can coexist with Virtualisation technology
CPU extension such as VT-x/AMD-V, VT-D/AMD-Vi, VT-c can provide coexistence between RARE/freeRouter and a small amount of storage and compute node. (Such as micro-K8/docker)
In the next article we will start our journey in creating a carrier grade CPE using the platform above.