HANDS ON FOR INTERESTED USERS
The Social Identities pilots This pilot aims at demonstrating possible mechanisms to include Social Identities ( FB, Google, Linkedin..) in the Authentication and Authorization process for consuming federated services (SAML SPs)providing federated access to resources within a given research collaboration, exploiting mechanisms to enhance the LoA of the users. The idea is to be able to support individual researchers that are not affiliated with any of the traditional home organisations, as well as those users whose Identity Providers are not part of any of the eduGAIN participating federations.
The architecture implemented by the pilot provides an IDP/SP proxy which bridges the external ID providers through the usage of an Attribute Authority (COMANAGE).
At this purpose we have set up a specific collaboration inside COMANAGE, which acts as Attribute Authority, integrating the basic attributes
A VO sponsor is the admin of that Collaboration : identities are managed by the admin in the COMANGE admin interface at https://am03.pilots.aarc-project.eu/registry/
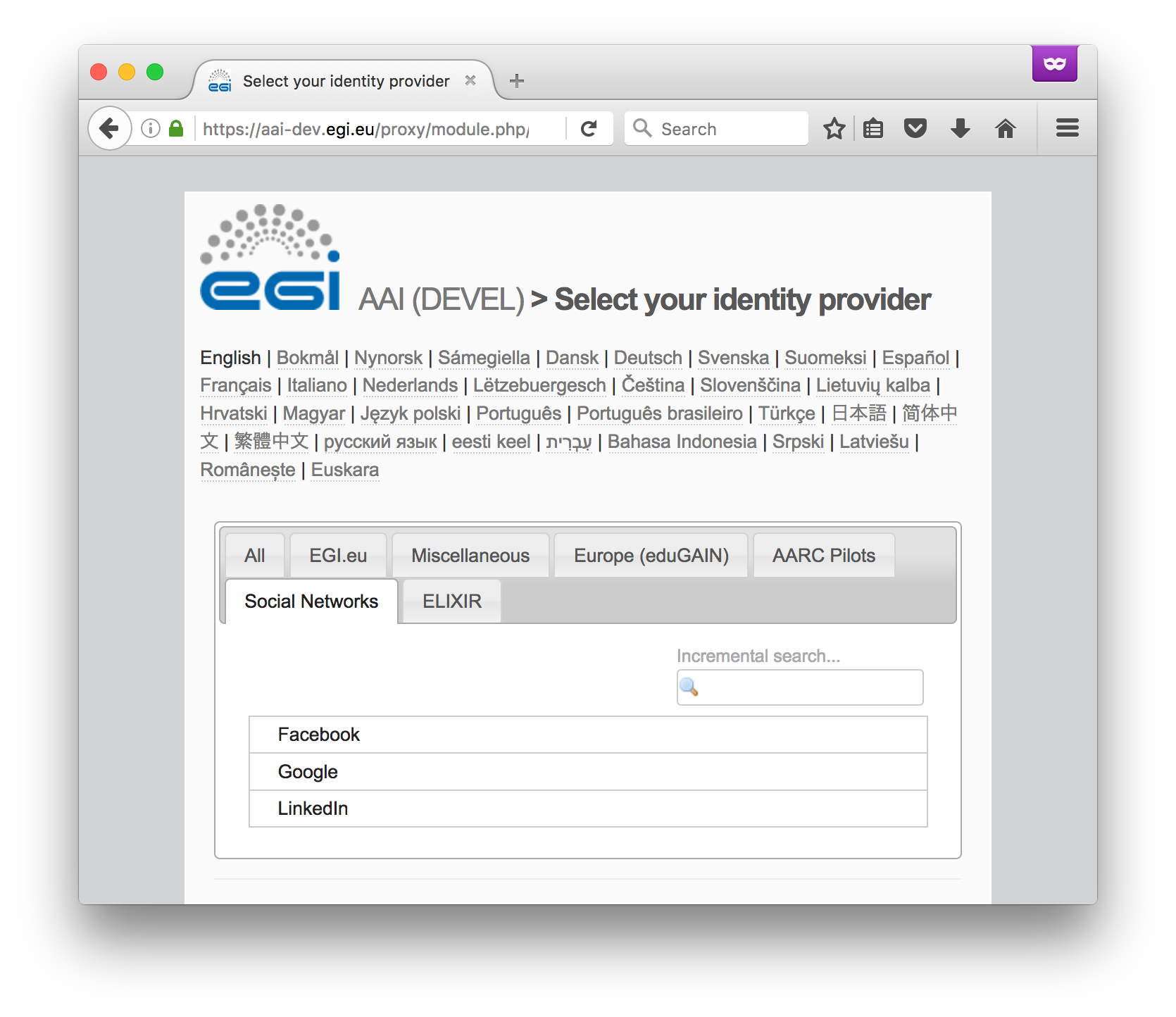
Users will need to access the openstack dashboard - ARAC instance at EGI ; They will be re-directed to the WAYF offering different IDPs; They will select on of the social ones ( e.g. Google ), and be then faced with their Google login page.
Once logged in, they will be displayed a message stating their request for subscription to the COMANAGE- collaboration requires approval by the VO Sponsor (and be informed of this also via email ).
Once approved, they will be notified via email - Once approved they will be able to access the dashboard
pilot showcases how to cater for these cases by enabling a research collaboration, namely the AARC Pilot User Community, to use social networks as third party Identity Providers. The key factors in enabling such Guest Identity services is to be able to support multiple technologies and flexible policies in a scalable and trustworthy manner. In this context, the pilot is based on an SP-IdP proxy architecture (see also AARC Blueprint Architecture) through which users are able to authenticate with the credentials provided by the IdP of their Home Organisation (e.g. via eduGAIN), as well as using Social Identity providers, or other selected external identity providers. Specifically, the proxy has built-in support for SAML, OpenID Connect and OAuth2 providers and enables user logins through Facebook, Google, LinkedIn, and ORCID. The proxy is then responsible for enriching the identity information that comes from these external IdPs with additional attributes, including the following:
- a unique, persistent, non-reassignable user identifier (AARC ID, expressed as an
eduPersonUniqueIdattribute); - assurance level (expressed as an
eduPersonAssuranceattribute); - community membership roles and groups (expressed through
eduPersonEntitlementattribute values).
Note that a user cannot access federated resources until they obtain an AARC ID through enrollment in the AARC Pilot User Community. In addition, we have defined a minimum set of attributes required for registering for an AARC ID. The SP-IdP proxy will attempt to retrieve these attributes from the user’s Home Organisation. If this is not possible, then the user will be asked to provide the missing attribute values and the request to join the collaboration will need to go through a verification process by the collaboration's Sponsors.
For the purpose of this pilot, we have enabled federated access to the dashboard of a demo OpenStack Cloud deployment. Specifically, the pilot IdP proxy has been configured to authenticate users and communicate the result of the authentication to OpenStack's Identity service (Keystone) using SAML assertions. The SAML assertions are then mapped to keystone user groups based on which the authenticating user can access cloud resources using their federated AARC ID.
User Workflow for interested users:
| 1. | Access the Openstack Dashboard to use the Openstack cluster configured as a SAML SP OpenStack's Dashboard (Horizon) at https://am02.pilots.aarc-project.eu/horizon | |
| 2. | Click Connect and select your Identity Provider from the discovery page (WAYF). You may select any of the following options:
| |
| 3. | You will be redirected to the Sign In page of your IdP Enter your login credentials to authenticate yourself with the IdP of your Home Organisation (e.g. Google) | |
| 4. | After successful authentication, you may be prompted by your Home Organisation to consent to the release of personal information to the EGI AAI Service Provider Proxy | |
| 5. | On the EGI AAI Consent about releasing personal information page, click Yes, continue to consent to the release of personal information to the EGI User Account Registry. If you select the Remember option, your browser will remember your choice unless you clear your cookies or restart the browser. | |
| 6. | If this is your first time logging in, you will be redirected to the AARC Pilot User Community Sign Up page after succesful successful authentication. Alternatively, you may access the sign up page directly by visiting: | |
| 57. | Depending on the LoA and/or attributes released by your Home IdP, there are two sign up workflows:
| |
| 68. | If your sign up request requires approval (second workflow), the Sponsors of the VO will be notified via email | |
| 79. | One of the Sponsor users has to approve your request via the COmanage Registry at https://aai-dev.egi.eu/registry | |
| 810. | After approval, your account will be activated in COmanage - Subject Identifier retained by Google - Unique, Persistent, non-Reassignable (not the email address of google) | |
| 911. | Relogin to OpenStack's dashboard at https://am02.pilots.aarc-project.eu/horizon | |
| 1012. | You will be mapped to a Keystone user group based on the values of the eduPersonEntitlement attribute |