| Table of Contents |
|---|
Introduction
Hybrid Authentication is an operational scenarios many libraries are currently involved in: online publishers resources can be accessed both via IP based authentication and through a Web Single-Sign-On Session. AARC aims at promoting the adoption of federated credentials in accessing services; This pilot shows how Libraries can effectively use the OCLC EZproxy tool (which they often already have available, acting as an IP proxy) by levering its Acces Mode Switch feature, once configured accordingly. EZproxy can this act as a switch from IP based proxy to access non federated resources to SAML SSO redirect proxy, to entitle users to federated online resources if they own SAML2-IDP provided credentials.
This feature is of great potential in pushing libraries towards the adoption of federated identities and the provisioning of federated credentials to their users: EZproxy is a very popular tool widely adopted by Libraries worldwide, so the goal of this pilot is to show that, after proper configuration, it enables libraries to provide services to their users via Identity Federations and SAML IDPs.
Detailed description
A detailed description of the aim and approach of this pilot and how it maps to the AARC Blueprint Architecture is available here
Demonstration Portal
Workflow
For federated users
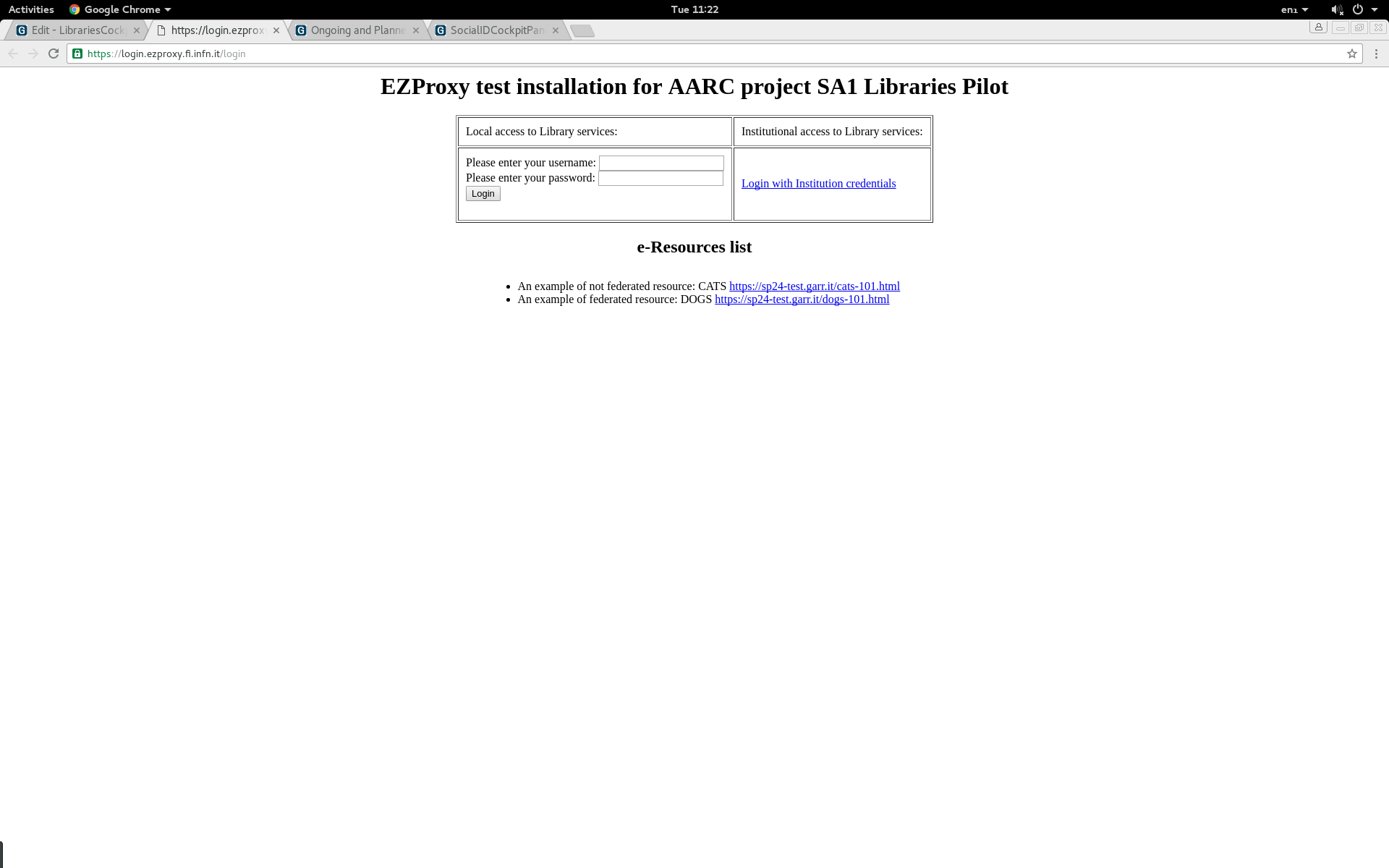
| 1. | Access EZ proxy demo instance at https://ezproxy.fi.infn.it/ | |
| 2. | Login to EZproxy portal with your federated ID:
| |
| 3. | Choose the Federated Resource Dogs 101 (redirection to SSO) (note the URL http://ezproxy.fi.infn.it/login?url=https://sp24-test.garr.it/dogs-101.html )
| |
| 4. | Choose the Not Federated Resource Cats 101 (via proxy) (note the URL http://ezproxy.fi.infn.it/login?url=https://sp24-test.garr.it/cats-101.html )
| |
| 5. | ||
| 6. |
...
...
...
...
...
...
For non-federated users
...
Components
Benefits
Demo Video
https://drive.google.com/open?id=0B6nLU4k7ZZvfaUM4OTJtTmlFN28
Transcript https://drive.google.com/open?id=0B6nLU4k7ZZvfcGNybTFXZ0VaRlk
=================================================================================================================
Scenario A FEDERATED USER
...
...
When she accesses
-> A.1] a FEDERATED RESOURCE, by means of SAML SSO session, she gets access to the resource with SAML authentication;
-> A.2] a NOT FEDERATED RESOURCE restricted to authorised IPs, by means of REWRITING properties of the proxy she gets access to the resource because she's authorized having the IP address of the proxy.
The USER: you with your federated credential
...
| 1. |
...
| Access EZ proxy demo instance at |
The federated resource is: DOGS https://sp24-test.garr.it/dogs-101.html (Access protected by SAML SSO authentication)
The not federated resource is: CATS https://sp24-test.garr.it/cats-101.html (Access forbidden, access permitted only through authorised IPs)
...
| 2. | Login to EZproxy portal as a library walk-in guest:
| |
| 3. | Choose the Federated Resource Dogs 101 (redirection to SSO) (note the |
...
URL http://ezproxy.fi.infn.it/login?url=https://sp24-test.garr.it/dogs-101.html )
|
...
|
...
|
...
| |
| 4. | Choose the Not Federated |
...
Resource Cats 101 (via proxy) (note the |
...
URL http://ezproxy.fi.infn.it/login?url=https://sp24-test.garr.it/cats-101.html )
|
Scenario B] NON-FEDERATED USER
in this case the user is not provided with Federated access and is permitted via her IP address.
The USER: you connecting from an authorized IP address (for the simulation please send a email to Barbara Monticini with your IP address)
The EZproxy portal is: https://ezproxy.fi.infn.it/, access through "Institutional login"
The federated resource is: https://sp24-test.garr.it/dogs-101.html
The not federated resource is https://sp24-test.garr.it/cats-101.html (access permitted only through the IP of the proxy)
- login to "Institutional login", you will be redirected to the idp and will be recognized as library-walk-in user
- Choose the Federated Resource Dogs 101 (redirection to SSO) https://sp24-test.garr.it/dogs-101.html
- note the URL on the address bar of the browser:
- if you see ezproxy.fi.infn.it, then your page is rewrited by the proxy
- if you dont see ezproxy.fi.infn.it, this means that you got a SAML SSO session
- note the URL on the address bar of the browser:
- Choose the Not Federated Resource Cats 101 (via proxy) https://sp24-test.garr.it/cats-101.html
- note the URL on the address bar of the browser. You are permitted to access thanks to the rewriting rule of the proxy and you get the page from the Resource via IP address authorization (accepted and authorized on the idp)
Components
Benefits
Demo Video
https://drive.google.com/open?id=0B6nLU4k7ZZvfaUM4OTJtTmlFN28
Transcript https://drive.google.com/open?id=0B6nLU4k7ZZvfcGNybTFXZ0VaRlk
Benefts
- A user use only one unified method of authentication to access both federated and not federated resources
- For each resource the Library logs the access in a unified way. If a Resource is federated, only federated access will be allowed, and IP based auth wont be permitted anymore. If a Resource is not federated, the user gets the access via IP address auth, and the proxy will log the access o that resource in this way.
...
- .
...