Overall goals and approach of Pilots in AARC
Aims
The Pilots activity aims at facilitating researchers by providing the access management tools and framework to support collaborative research in a distributed environment. To this end, in this activity we demonstrate through (pre-) production services that:
existing AAIs and authentication sources can be leveraged to enable (SSO) access with appropriate level of assurance for any natural person (academia and non-academia) to shared resources offered by different e-Infrastructure providers and communities. (task 1)
authoritative decisions and user/group context can be based on distributed group managers and attribute providers. (task 2)
access to non-web and commercial e-infrastructure services can be enabled. This requires the bridging of SAML (NREN world) and token/certificate based (e-infra world). (task 3)
Approach
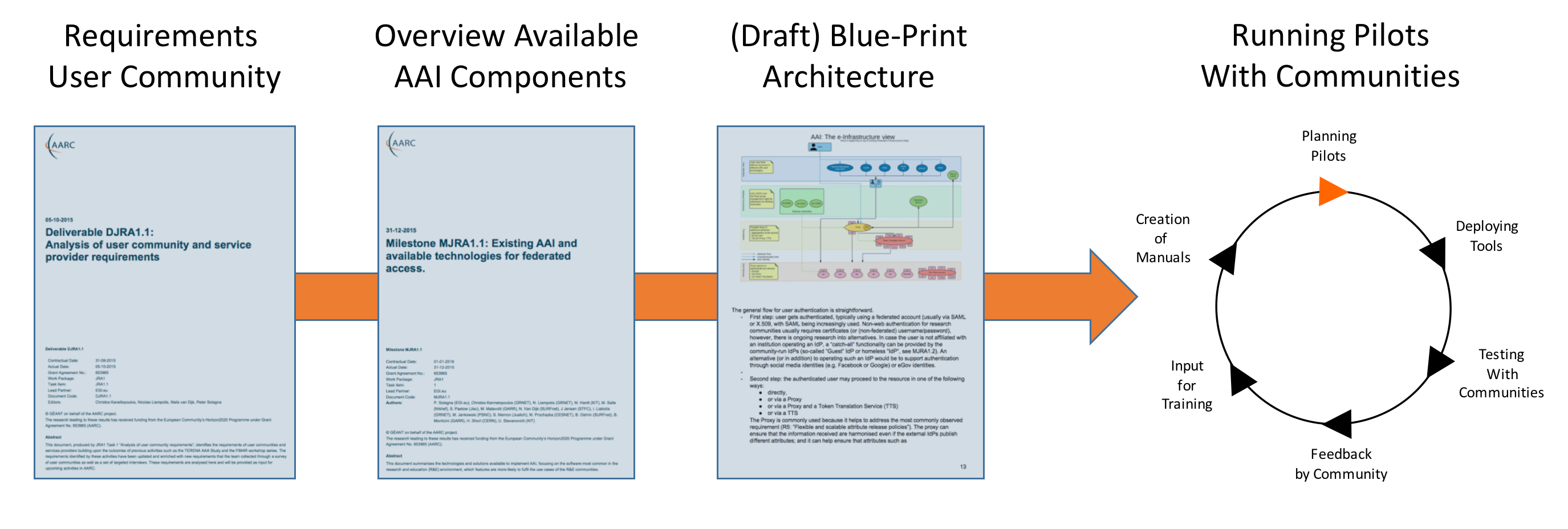
The approach consists of deploying existing components as discussed with and identified by JRA1 and to integrate a selection of these components according to a common architecture that has been drafted in JRA1. To this purpose we established a stable pilot environment with solutions to be tried and assessed by stakeholders of the research communities. A more detailed description of the aims and approach of the pilots activity is available here: Specify the work to be undertaken in collaboration with JRA1 and NA3
- Analysis of user- community requirements
- Existing AAI and available technologies for federated access
- First Draft of the blueprint architecture (a 2nd revised version is currently in preperation)
Pilots started
Based on the guiding documents of the AARC architecture (JRA1) and the AARC policy harmonisation (NA3) activities we commenced the first pilot cycles:
- In task 1 "Guest Access" we started a pilot to involve Libraries in the identification and hands-on implementation of relevant solutions to support their migration from IP-based authentication against publishers' online resources to a SAML/federated based approach. This work focuses on embracing all possible users that need access to library resources (including so-called walk-by users which may be citizen scientists) and all relevant service providers, including those who only support IP-address based access control. With this pilot we want to show that it is possible to apply the principle of inclusiveness and at the same hide complexity for the user.
More details on the status of this work are available here - In task 2 "Attribute Management" we pilot the use of SAML based attribute authorities to provide authoritative information e.g. to be consumed by cloud services at EGI. The Attributes Authorities (AAs) used in this context are PERUN and COmanage (or even ORCID as an AA). Attribute aggregation components used are OpenConext and SimpleSAMLphp. At later phase we aim to address and pilot scenarios where attributes from multiple attribute authorities (and probably multiple VOs) flow into service. E.g. consider a cloud provider that wants to serve several Virtual Organizations, managed by different Virtual Organization Manager Entities.
- In task 3 "Access to Resources" quite some progress has been made in establishing token translation pilot services. One pilot focuses on the application of CI-Logon components + add-ons to bridge the gap between the world of SAML based authentication (NRENs) and that of certificate based authentication (GRID and e-infrastructure providers). A description of our intermediate results are available in this blog and this presentation. In a second pilot on access to resources, we assess the feasibility to enable non-web single sign-on based on LDAP Facade, developed by the Karlsruhe Institute of Technology. At the same time we started to engage a number of service providers to pilot with provisioning their services as a service provider or attribute authority. One example is ORCID. ORCID.org offers researchers a persistent life long digital ID. Providing access to ORCID with a federated account and including ORCID as an Attribute Authority may provide interesting clues for Research Communities & AAIs. Read more about the pilot with ORCID in AARC: see powerpoint
With these efforts we identified interesting clues but also a number of challenges we need to solve to be able to bridge different research infrastructures and communities. A brief overview of all ongoing and planned pilots is available here. Further details and updates will follow soon.
More details per task are available here: