Starting from SOHO #008, everyone inside home network can:
- reach the Internet thanks to NAT translation described in SOHO #004
- reach now their favorite Internet service by name thanks for SOHO #005
- and get IPv4 (or IPv6) address from DHCP server (we took as a switch connected to sdn6)
- this applies to all wired host but also all mobile host connected to the home wireless network
- And you get a Great UPNP server forwarder
Requirement- Basic Linux/Unix knowledge
- Service provider networking knowledge
| | |
Overview
Wireguard gained a lot popularity and attention when it went into Linux kernel in March 2020. And pure coincidence or not, 1 month later, Wireguard made its way through ubuntu 20.04 LTS. Csaba MATE, freeRtr maintainer took "the Taurus by his horns" (sorry for the pure French translation of the proverb  ) and in turn, he added Wireguard support into freeRtr few months later ...
) and in turn, he added Wireguard support into freeRtr few months later ...
In the current pandemic context, Wireguard is highly used to establish software VPN connectivity toward office resources. In my context, among other usages, I'm using it in order to reach DN42, an overlay network very good for learning protocol like BGP and explore routing technology.
Article objective
There are plenty of web resources debating Wireguard based VPN topics. The purpose of this article will simply put the focus on how to configure a Wireguard tunnel between:
- ubuntu 20.04 host
- RARE/freeRtr
Diagrams
In this example, I'll use my home router as Wireguard tunnel end point and a ubuntu 20.04 server in my home LAN.
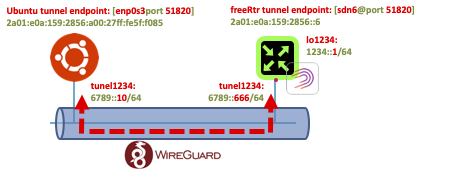
The steps at RARE/freeRtr level are:
- configure vrf v1234.
- configure loopback1234 with IPv6 network 1234::666/64 at freeRtr level and bind it to vrf v1234
- configure Wireguard crypto stanza
- configure tunnel1234
- with Wireguard crypto stanza defined above,
- configure tunnel source, destination underlay in vrf inet
- finally configure tunnel interface in vrf v1234
- As RARE/freeRtr is oriented toward the future we will just forget about legacy IPv4, therefore the underlay tunnel will be established with IPv6 only. (←Joke
 )
)
[ SOHO #009 ] - "Network 1234::/64 ? Please follow tunnel1234 Wireguard tunnel !"
Step -1- Set up ubuntu 20.04 Wireguard end point
sudo apt-get update
sudo apt-get upgrade
sudo apt install wireguard
- generate for ubuntu private/public key pair
umask 077
wg genkey > ubi20-private-key
wg pubkey < ubi20-private-key > ubi20-public-key
- generate for freeRtr private/public key pair
umask 077
wg genkey > freertr-private-key
wg pubkey < freertr-private-key > freertr-public-key
- edit ubuntu 20.04 Wireguard configuration
cat /etc/wireguard/wg0.conf
[Interface]
Address = 6789::10/64
PrivateKey = <ubuntu-private-key>
ListenPort = 51820
[Peer]
PublicKey = <freertr-public-key>
AllowedIPs = 1234::/64,6789::/64
Endpoint = 2a01:e0a:159:2856::6:51820
- Activate wireguard tunnel
Step -2- Configure RARE/freeRtr Wireguard endpoint
- First thing first configure vrf v1234
!
vrf definition v1234
exit
!
- Configure loopback1234 and bind it to vrf v1234
!
interface loopback1234
description Wireguard allowed IPv6 network
vrf forwarding v1234
ipv6 address 1234::1 ffff:ffff:ffff:ffff::
no shutdown
no log-link-change
exit
!
- Configure Wireguard crypto stanza
!
crypto ipsec wg-1234
key <freertr-private-key><ubuntu-public-key>
replay 0
exit
!
- Configure tunnel1234 Wireguard tunnel
!
interface tunnel1234
description RARE/freeRtr Wireguard tunnel
tunnel key 51820
tunnel vrf inet
tunnel protection wg-1234
tunnel source sdn6
tunnel destination 2a01:e0a:159:2856:a00:27ff:fe5f:f085
tunnel mode wireguard
vrf forwarding v1234
ipv6 address 6789::666 ffff:ffff:ffff:ffff::
no shutdown
no log-link-change
exit
!
- if you are using a dataplane please add Wireguard tunnel and corresponding VRF in "server p4lang p4"
!
server p4lang p4
...
export-vrf v1234 5
...
export-port tunnel1234 45 0 0 0 0
...
exit
!
! Where 45 is an ID not already used in server p4lang
Verification
Verification @ ubuntu 20.04
- Check Wireguard interface
wg0: flags=209<UP,POINTOPOINT,RUNNING,NOARP> mtu 1420
inet6 6789::10 prefixlen 64 scopeid 0x0<global>
unspec 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00 txqueuelen 1000 (UNSPEC)
RX packets 980 bytes 44240 (44.2 KB)
RX errors 204 dropped 0 overruns 0 frame 204
TX packets 191 bytes 15768 (15.7 KB)
TX errors 0 dropped 64 overruns 0 carrier 0 collisions 0
- Check ipv6 routing @ ubuntu
::1 dev lo proto kernel metric 256 pref medium
1234::/64 dev wg0 metric 1024 pref medium
2a01:e0a:159:2856::/64 dev enp0s3 proto ra metric 100 expires 2419185sec pref medium
6789::/64 dev wg0 proto kernel metric 256 pref medium
fe80::/64 dev enp0s3 proto kernel metric 256 pref medium
fe80::/64 dev enp0s8 proto kernel metric 256 pref medium
default via fe80::24c:73ff:fe07:a77 dev enp0s3 proto ra metric 100 expires 1785sec mtu 1500 pref medium
- ping freeRtr tunnel endpoint
PING 6789::666(6789::666) 56 data bytes
64 bytes from 6789::666: icmp_seq=1 ttl=255 time=2.07 ms
64 bytes from 6789::666: icmp_seq=2 ttl=255 time=1.99 ms
64 bytes from 6789::666: icmp_seq=3 ttl=255 time=2.20 ms
64 bytes from 6789::666: icmp_seq=4 ttl=255 time=2.26 ms
- ping cascaded loopback1234
PING 1234::1(1234::1) 56 data bytes
64 bytes from 1234::1: icmp_seq=1 ttl=255 time=2.04 ms
64 bytes from 1234::1: icmp_seq=2 ttl=255 time=1.92 ms
64 bytes from 1234::1: icmp_seq=3 ttl=255 time=2.10 ms
64 bytes from 1234::1: icmp_seq=4 ttl=255 time=1.96 ms
Congratulations !
Now let's proceed to verification at freeRtr level
Verification @ freeRtr
- Check Wireguard interface
tunnel1234 is up (since 05:18:05, 1 changes)
description:
type is wireguard, hwaddr=none, mtu=1400, bw=8000kbps, vrf=v1234
ip4 address=7.8.9.254/24, netmask=255.255.255.0, ifcid=1052271466
ip6 address=6789::666/64, netmask=ffff:ffff:ffff:ffff::, ifcid=823043043
received 28 packets (2488 bytes) dropped 0 packets (0 bytes)
transmitted 665 packets (51318 bytes) promisc=false macsec=false
- Check ipv6 routing @ freeRtr
typ prefix metric iface hop time
C 1234::/64 0/0 loopback1234 null 02:20:16
LOC 1234::1/128 0/1 loopback1234 null 02:20:16
C 6789::/64 0/0 tunnel1234 null 01:25:49
LOC 6789::666/128 0/1 tunnel1234 null 01:25:49
- Check IPv6 underlay reachability in vrf inet
typ prefix metric iface hop time
S ::/0 1/0 sdn1 2a01:e0a:159:2850::1 05:21:27
...
C 2a01:e0a:159:2856::/64 0/0 sdn6 null 05:21:27
LOC 2a01:e0a:159:2856::6/128 0/1 sdn6 null 05:21:27
...
- ping ubuntu 20.04 tunnel endpoint
pinging 6789::10, src=null, vrf=v1234, cnt=5, len=64, tim=1000, gap=0, ttl=255, tos=0, fill=0, sweep=false, multi=false, detail=false
!!!!!
result=100%, recv/sent/lost/err=5/5/0/0, rtt min/avg/max/total=2/2/2/10
Congratulations !
Conclusion
In this article we learned how to configure a Wireguard tunnel between ubuntu 20.04 and RARE/freeRouter. Configuring Wireguard is a simple 2 steps operation:
- Configure Wireguard crypto stanza
- and bind it to a Wireguard tunnel
) and in turn, he added Wireguard support into freeRtr few months later ...
)


