Create a copy of this page as a sibling and fill in that copy as instructed below.
Describe the platform
To ensure a successful test of the authenticator, please follow these steps:
- Prepare the authenticator that you wish to test. It is recommended to use it only for this test to avoid any conflicts. If necessary, delete the passkey and reset the authenticator's settings (e.g., disable PIN, unregister fingerprint). Sounds scary. What i I already have something on it, or had some UV method set?
- It may be a hardware authenticator, such as a YubiKey.
- It may be an operating system authenticator, such as Touch ID or Windows Hello.
- It may be a software authenticator, such as tpm-fido.
- It may be a password manager with passkey support, such as Dashlane.
- Fill in the details in the table below:
$$Tester: | test line 1 test line 2 |
|---|---|
| $$Date: Use '//' wiki date$$ | test line 1 test line 2 |
| $$Authenticator (or device) vendor: Yubico, Apple, Dell, HP, Android phone brand...$$ | |
| $$Authenticator (or device) model: YubiKey 5, iPhone 13, PC model name, MacBook year size, MacBook Air year size, MacBook Pro year size...$$ | test |
| $$OS and its version: iOS 13, macOS 10.5.8, Windows 10 22h2, Windows 11 22h2, Android 13...$$ | test |
| $$Browser and its version: Chrome 114, Firefox 114...$$ | test |
| $$I registered a PIN/password/finger/face in the authenticator before the session: (I guess that should be set for the entire session! Should there be 2 sessions per device? I also guess that phones require some form of screen lock. Perhaps require both options only for security keys?) Enter yes or no$$ | test line 1 test line 2 test line 3 |
$$
- Be prepared to capture screenshots of each system/browser dialogue that appears. (Later in this process, you will register a passkey multiple times)
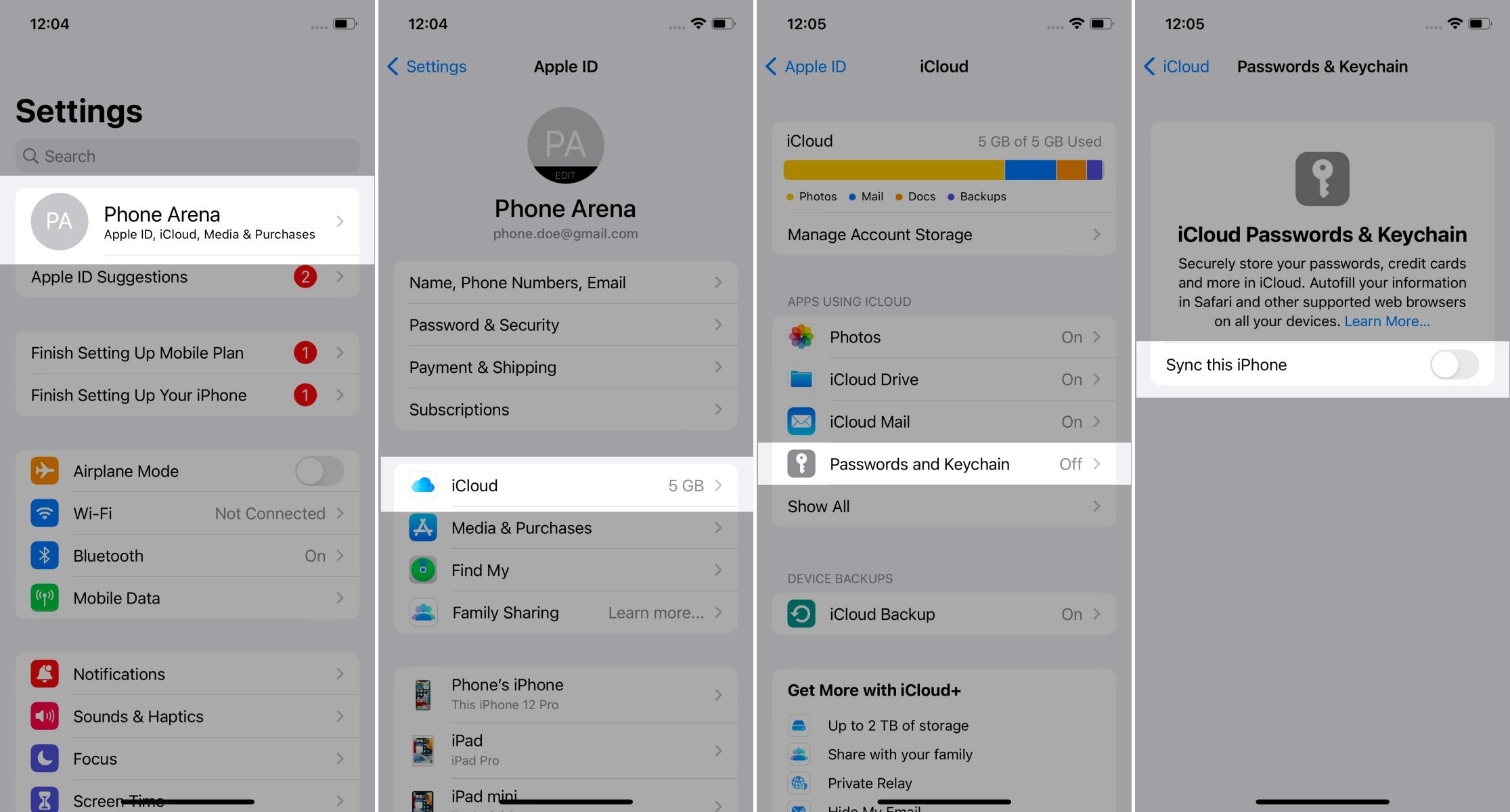
Capture the platform or browser passkey options
- If there are any options or settings related to "passkeys", "security keys" or similar in your OS/device/spaceship settings, capture screenshots and attach them here.
- If there are password manager options, only capture them.
- If there are browser options, capture them instead.
- If there are operating system options, capture them instead.
This is an exemplary path, screenshot only the screen(s) with passkey options (the last one below):
Paste system options screenshots on the right: | test line 1 test line 2 test line 3 |
|---|
Get diagnostics
- Open https://webauthntest.identitystandards.io/.
- Click the "..." button.
$$Copy-paste the diagnostic results on the right as text (rows are labeled the same, but you may have different values): Platform authenticator (isUVPAA) Available Conditional Mediation (Autofill UI) Not defined CTAP2 support (Firefox) Supported $$ | test line 1 test line 2 test line 3 |
|---|
$$
Set repeated settings
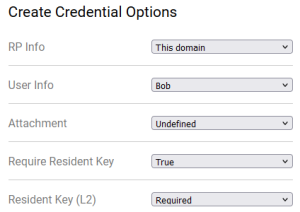
- Click the "+" button to create a passkey. Choose the following values:
- RP Info: This domain
- User Info: Bob
- Attachment: undefined
- Require Resident Key: true
- Resident Key (L2): required
It should look like this:
Create passkeys using various settings
If you encounter an error message like "Authenticator data cannot be parsed", it indicates that the combination of arguments used is not supported by the authenticator being tested.
Test User Verification
- Select User Verification: Discouraged and click CREATE.
- I think we should request screenshots at only one creation test, you choose where. Probably not here but in the next creation!!!
Paste screenshot(s) on the right: | test line 1 test line 2 test line 3 |
|---|
- Copy-paste the result from the web app.
$$UVUCopy-paste the result on the right: | test line 1 test line 2 test line 3 |
|---|
- $$Select User Verification: Required and click CREATE.
- Copy-paste the result from the web app.
$$UVRCopy-paste the result on the right: | test line 1 test line 2 test line 3 |
|---|
$$
- Should this remain? User Verification: Required
AND SO ON...
Test Attestation
- Select Attestation: Enterprise and click CREATE.
- Copy-paste the resulting registration data into row 3. Attestation: Enterprise, or input "unsupported" if there was an error.
- Select Attestation: Direct and click CREATE.
- Copy-paste the resulting registration data into row 4. Attestation: Direct, or input "unsupported" if there was an error.
- Select Attestation: Indirect and click CREATE.
- Copy-paste the resulting registration data into row 5. Attestation: Indirect, or input "unsupported" if there was an error.
- Select Attestation: None and click CREATE.
- Copy-paste the resulting registration data into row 6. Attestation: None, or input "unsupported" if there was an error.
- If none of the previous four tries worked, select Attestation: Undefined and click CREATE.
- Copy-paste the resulting registration data into row 6. Attestation: None, or input "unsupported" if there was an error.
- If Attestation: Direct worked, select it; otherwise, if Attestation: Indirect worked, select it; otherwise select Attestation: Undefined.
Test CredProtect Extension
- Select CredProtect Extension: userVerificationOptional and click CREATE.
- Copy-paste the resulting registration data into row 7. CredProtect Extension: userVerificationOptional, or input "unsupported" if there was an error.
- Select CredProtect Extension: userVerificationOptionalWithCredentialIDList and click CREATE.
- Copy-paste the resulting registration data into row 8. CredProtect Extension: userVerificationOptionalWithCredentialIDList, or input "unsupported" if there was an error.
- Select CredProtect Extension: userVerificationRequired and click CREATE.
- Copy-paste the resulting registration data into row 9. CredProtect Extension: userVerificationRequired, or input "unsupported" if there was an error.
- If none of the previous three tries worked, select CredProtect Extension: Undefined and click CREATE.
- Copy-paste the resulting registration data into row 7. CredProtect Extension: userVerificationOptional, or input "unsupported" if there was an error.
- Select CredProtect Extension: Undefined (if not selected already).
Test cryptography
- Uncheck all the following checkboxes: Use ES256, Use ES384, Use ES512, Use RS256, Use EdDSA.
- Check Use ES256 and click CREATE.
- Copy-paste the resulting registration data into row 10. ES256, or input "unsupported" if there was an error.
- What about Use ES256 now? Clear it?
- Check Use ES384 and click CREATE.
- Copy-paste the resulting registration data into row 11. ES384, or input "unsupported" if there was an error.
- Check Use ES512 and click CREATE.
- Copy-paste the resulting registration data into row 12. ES512, or input "unsupported" if there was an error.
- Check Use RS256 and click CREATE.
- Copy-paste the resulting registration data into row 13. RS256, or input "unsupported" if there was an error.
- Check Use EdDSA and click CREATE.
- Copy-paste the resulting registration data into row 14. EdDSA, or input "unsupported" if there was an error.
I would skip this, and if needed, place some identifying labels above for easier extraction from test results pages.
The results will be aggregated into the summarised table below.
| Platform authenticator (isUVPAA) | |
|---|---|
| Conditional Mediation (Autofill UI) | |
| CTAP2 support (Firefox) | |
1. User Verification: Discouraged | |
| 2. User Verification: Required | |
| 3. Attestation: Enterprise | |
| 4. Attestation: Direct | |
| 5. Attestation: Indirect | |
| 6. Attestation: None | |
| 7. CredProtect Extension: userVerificationOptional | |
| 8. CredProtect Extension: userVerificationOptionalWithCredentialIDList | |
| 9. CredProtect Extension: userVerificationRequired | |
| 10. ES256 | |
| 11. ES384 | |
| 12. ES512 | |
| 13. RS256 | |
| 14. EdDSA |