You are viewing an old version of this page. View the current version.
Compare with Current
View Page History
Version 1
Current »
Create a copy of this page as a sibling and complete it as instructed below. Please do not disturb markers such as {10{ and }}.
To ensure a successful test of the authenticator, please follow these steps:
- For this test, you need a computer or mobile device and a hardware or software authenticator. It may be:
- Hardware authenticator, such as YubiKey.
- Operating system authenticator, such as Touch ID or Windows Hello.
- Software authenticator, such as tpm-fido.
- Password manager with passkey support, such as Dashlane.
- The actions performed during this test are parts of regular usage and should not affect the authenticator in any way. However, you may choose to use a brand-new authenticator, reset or clear it to avoid any conflicts during the test.
- If necessary, delete the passkey that you create during this testing if it prevents you from creating it again. This should not happen, but if it does, please provide a screenshot and an accompanying note. If you are willing to, reset the authenticator's settings (e.g., disable PIN, unregister fingerprint).
- Fill in the details in the table below:
Tester:
@ (name yourself){10{ | |
|---|
}}Date:
Use '//' to input date{15{ | |
|---|
}}Authenticator (or device) vendor:
Yubico, Apple, Dell, HP, Android phone brand...{17{ | Feitian |
|---|
}}Authenticator (or device) model:
YubiKey 5 NFC, iPhone 13, PC model name, MacBook year size, MacBook Air year size, MacBook Pro year size...{20{ | ePass Plus K9D |
|---|
}}OS and its version:
iOS 13, macOS 10.5.8, Windows 10 22H2, Windows 11 22H2, Android 13...{25{ | Ubuntu 22 |
|---|
}}Browser and its version:
Chrome 114, Firefox 114...{30{ | Firefox 117 |
|---|
}}I registered a PIN/password/finger/face in the authenticator before the session:
Yes or No
(The situation where you have not previously registered in the authenticator is interesting for checking if the passkey creation will trigger user registration.){35{ | No |
|---|
}}
- Be prepared to capture screenshots of each system/browser dialogue that appears. Later in this process, you will register a passkey multiple times.
- If there are any options or settings related to "passkeys", "security keys" or similar in your OS/device/spaceship settings (related to the authenticator you are going to use), capture screenshots and paste or attach them here.
- If you are using a password manager, capture its passkey-related options.
- If you are using a browser supporting passkeys, capture its options instead.
- If you are using an operating system to manage passkeys, capture its options instead.
Possible locations:
- Windows 11: Settings > Accounts > Passkeys
- iOS: Settings > Apple ID > iCloud > Passwords & Keychain
- Chrome (Windows): Settings > Autofill and passwords > Password Manager > Manage passkeys
These are exemplary paths. You need to screenshot the only passkey-related options. Please paste screenshots in or outside this table as suitable:
Get diagnostics
- Open https://webauthntest.identitystandards.io/.
- Log in using any user name - this is probably just for the app's internal logging.
- Click the "..." button.
- If there are any problems while doing the above, try another time or use another device. If the problem persists, please let us know over Slack.
}}Copy-paste the diagnostic results on the right as text (rows are labelled the same): Platform authenticator (isUVPAA)
Conditional Mediation (Autofill UI)
CTAP2 support (Firefox)
{40{ |
Not available Not defined Supported |
|---|
}}
Set repeated settings
- Click the "+" button to create a passkey. Choose the following:
- RP Info: This domain
- User Info: Bob
- Attachment: Undefined
- Require Resident Key: True
- Resident Key (L2): Required
It should look like this:
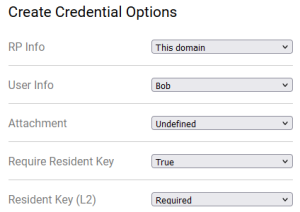
Create passkeys using various settings
- Capture and paste below the screenshot of various prompts, screens, dialogues, questions or messages that show up during passkey registration as you encounter them.
Please insert or paste screenshots in this table as suitable, preferably putting the related screenshots in one row (you can place a note beneath an image in the same cell):
| Seq1 | | | | |
|
|
| Seq2 (just new screens) |
|
|
|
|
|
|
| Seq3 (just new screens) |
|
|
|
|
|
|
| Seq4 (just new screens) |
|
|
|
|
|
|
Test User Verification
- Select User Verification: Discouraged and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{45{ | Credential ID
3D13A9358E304E23B0FE8EAA9D3A7E93AB7CBDA7885B007B8BE67A106D26C453 RP ID
webauthntest.identitystandards.io AAGUID
EE041BCE-25E5-4CDB-8F86-897FD6418464 Credential Registration Data [more details]
Key Type: EC
Discoverable Credential: true
Attestation Type: none (unverified)
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=834 Last Authentication Data [more details]
No authentications |
|---|
}}
- Select User Verification: Required and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
- Note that the latest result is the rightmost in the bottom row. You may delete already pasted results.
- All authenticators should be able to register multiple passkeys for the same domain, so you do not need to delete the previously created one. It is likely that the passkeys you create will override each other since they are for the same domain and use the same user name "bob@example.com").
Copy-paste the result on the right:
Put Unsupported if there was an error{50{ | Credential ID
EAAE4729D7650BB15F09840E04FEADDB6A9D59FB255D692348DCB7612D8264E8 RP ID
webauthntest.identitystandards.io AAGUID
EE041BCE-25E5-4CDB-8F86-897FD6418464 Credential Registration Data [more details]
Key Type: EC
Discoverable Credential: true
Attestation Type: none (unverified)
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1069 Last Authentication Data [more details]
No authentications |
|---|
}}
Test Attestation
- Select Attestation: Enterprise and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{55{ | Credential ID
1719D1040AB7C5D0646299D0C1E88ABA7906B0E15D21404A40866BF7CAA70310 RP ID
webauthntest.identitystandards.io AAGUID
EE041BCE-25E5-4CDB-8F86-897FD6418464 Credential Registration Data [more details]
Key Type: EC
Discoverable Credential: true
Attestation Type: packed
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1396 Last Authentication Data [more details]
No authentications |
|---|
If registration worked, click on "Credential Registration Data [more details]" and copy-paste the content of the dialogue:
| Require Resident Key
true Authenticator Data
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1396 Authenticator Data in Hex
0B997CCCEB3AEB29C55C94A894B11CF01A24B4C8AE706F328CC2EA8CEBC4AD5C4100000574EE041BCE25E54CDB8F86897FD641846400201719D1040AB7C5D0646299D0C1E88ABA7906B0E15D21404A40866BF7CAA70310A5010203262001215820DBDAFF24A0FFBC3A7CE03CE932E9681BFA36E34E34D9B01C7D5D094DD23681422258200B76D191573591191F87EDB5DC2894B7A49EC930E6F86BC6ED16CADD401D7448 Public Key
EC key: A5010203262001215820DBDAFF24A0FFBC3A7CE03CE932E9681BFA36E34E34D9B01C7D5D094DD23681422258200B76D191573591191F87EDB5DC2894B7A49EC930E6F86BC6ED16CADD401D7448 Extension Data
No extension data Attestation Statement Chain
[{"version":3,"subject":"/C=US/O=Feitian Technologies/OU=Authenticator Attestation/CN=FT FIDO2 0430","issuer":"/C=US/O=Feitian Technologies/CN=Feitian FIDO CA 04","extAaguid":{"critical":false,"oid":"1.3.6.1.4.1.45724.1.1.4","vidx":942}},{"version":3,"subject":"/C=US/O=Feitian Technologies/CN=Feitian FIDO CA 04","issuer":"/C=US/O=Feitian Technologies/CN=Feitian FIDO Root CA"}] Attestation Statement in Hex
A363616C67266373696758483046022100EB9EF2B1999CC72EE7112BAB7BBBA56FA32D1DBEB732A4AC2575DCCAE0C8D8FD022100978E1C9F3897FD931ABDE5957CCB9E0133654AD45B89B81252E7E02F6B758943637835638259023F3082023B308201E1A00302010202101DF2B55A51DC4B6885A3D99E697FED12300A06082A8648CE3D0403023049310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F67696573311B301906035504030C124665697469616E204649444F2043412030343020170D3138303532313030303030305A180F32303333303532303233353935395A3068310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F6769657331223020060355040B0C1941757468656E74696361746F72204174746573746174696F6E3116301406035504030C0D4654204649444F3220303433303059301306072A8648CE3D020106082A8648CE3D03010703420004B27E0E8E39001F54EC9B6F4FE8841903764520A876EB698D3CC00D7D5B4DC3CCD95632A31A13ACBD67F38F3D62B2A5A0DC0CA52896400DC9AD39788BEA288045A38189308186301D0603551D0E04160414DD3244171A67ABBF52200773D13CCF3796AE77B1301F0603551D2304183016801493237066C51DCEC4AB1C2BAD84C1F3E71DCE6067300C0603551D130101FF040230003013060B2B0601040182E51C0201010404030204303021060B2B0601040182E51C01010404120410EE041BCE25E54CDB8F86897FD6418464300A06082A8648CE3D040302034800304502203F16E910B2A1BD7FAC33D43DA681B9663867DD6FA2D7CB9D274707F7FCF1B1B1022100A33BB88152391FC652BB9B7DE31832E5026B9AD3E37AC94F25A6F44EABF344D65901FE308201FA308201A0A003020102021018152B41B743AE6DB41599C3B17D8209300A06082A8648CE3D040302304B310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F67696573311D301B06035504030C144665697469616E204649444F20526F6F742043413020170D3138303532303030303030305A180F32303338303531393233353935395A3049310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F67696573311B301906035504030C124665697469616E204649444F2043412030343059301306072A8648CE3D020106082A8648CE3D03010703420004C5A11656398A9216FC72BB28BA4A698539BF8F472B066CC8402A9DA49FD02433EBB54767470F5D877A9C4E2E9B7047D25AF85BCE203DC64551EAD9DB71EBB833A3663064301D0603551D0E0416041493237066C51DCEC4AB1C2BAD84C1F3E71DCE6067301F0603551D230418301680144BBD872611AD1C89CF0458BE70D2088C6B1623B730120603551D130101FF040830060101FF020100300E0603551D0F0101FF040403020106300A06082A8648CE3D040302034800304502207FB540C43F46961624BD132548B44ADF04B661718FE42C32BA5F9AD40C706AB5022100FAC5A67DDCD5C7F79158A4190568995BAEC753E27A954A4E3221F79E4A60C2F1 |
|---|
}}
- Select Attestation: Direct and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{60{ | Credential ID
6736CD11EE3386A12BDA5753C31D33F8B54B7E11DF0D8BA598E7E4BD4FFBBACA RP ID
webauthntest.identitystandards.io AAGUID
EE041BCE-25E5-4CDB-8F86-897FD6418464 Credential Registration Data [more details]
Key Type: EC
Discoverable Credential: true
Attestation Type: packed
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1412 Last Authentication Data [more details]
No authentications |
|---|
If registration worked, click on "Credential Registration Data [more details]" and copy-paste the content of the dialogue: | Require Resident Key
true Authenticator Data
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1412 Authenticator Data in Hex
0B997CCCEB3AEB29C55C94A894B11CF01A24B4C8AE706F328CC2EA8CEBC4AD5C4100000584EE041BCE25E54CDB8F86897FD641846400206736CD11EE3386A12BDA5753C31D33F8B54B7E11DF0D8BA598E7E4BD4FFBBACAA5010203262001215820B253ACA837372AF72D90E1336F21D20728ADAA480090D83C7C452F49D3321720225820613F62D1257A263ED05403F77008B60943D66D0A1861186CFADDFBEBA2665051 Public Key
EC key: A5010203262001215820B253ACA837372AF72D90E1336F21D20728ADAA480090D83C7C452F49D3321720225820613F62D1257A263ED05403F77008B60943D66D0A1861186CFADDFBEBA2665051 Extension Data
No extension data Attestation Statement Chain
[{"version":3,"subject":"/C=US/O=Feitian Technologies/OU=Authenticator Attestation/CN=FT FIDO2 0430","issuer":"/C=US/O=Feitian Technologies/CN=Feitian FIDO CA 04","extAaguid":{"critical":false,"oid":"1.3.6.1.4.1.45724.1.1.4","vidx":942}},{"version":3,"subject":"/C=US/O=Feitian Technologies/CN=Feitian FIDO CA 04","issuer":"/C=US/O=Feitian Technologies/CN=Feitian FIDO Root CA"}] Attestation Statement in Hex
A363616C67266373696758473045022100E6F27A5F4BA8B59B27EA7CC28120793B066A2611323A19721E7EA56DEDB481AC02206C35424251835195B427DB70C87E49D667E515459CC3265288983BC1A2AE4A2C637835638259023F3082023B308201E1A00302010202101DF2B55A51DC4B6885A3D99E697FED12300A06082A8648CE3D0403023049310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F67696573311B301906035504030C124665697469616E204649444F2043412030343020170D3138303532313030303030305A180F32303333303532303233353935395A3068310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F6769657331223020060355040B0C1941757468656E74696361746F72204174746573746174696F6E3116301406035504030C0D4654204649444F3220303433303059301306072A8648CE3D020106082A8648CE3D03010703420004B27E0E8E39001F54EC9B6F4FE8841903764520A876EB698D3CC00D7D5B4DC3CCD95632A31A13ACBD67F38F3D62B2A5A0DC0CA52896400DC9AD39788BEA288045A38189308186301D0603551D0E04160414DD3244171A67ABBF52200773D13CCF3796AE77B1301F0603551D2304183016801493237066C51DCEC4AB1C2BAD84C1F3E71DCE6067300C0603551D130101FF040230003013060B2B0601040182E51C0201010404030204303021060B2B0601040182E51C01010404120410EE041BCE25E54CDB8F86897FD6418464300A06082A8648CE3D040302034800304502203F16E910B2A1BD7FAC33D43DA681B9663867DD6FA2D7CB9D274707F7FCF1B1B1022100A33BB88152391FC652BB9B7DE31832E5026B9AD3E37AC94F25A6F44EABF344D65901FE308201FA308201A0A003020102021018152B41B743AE6DB41599C3B17D8209300A06082A8648CE3D040302304B310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F67696573311D301B06035504030C144665697469616E204649444F20526F6F742043413020170D3138303532303030303030305A180F32303338303531393233353935395A3049310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F67696573311B301906035504030C124665697469616E204649444F2043412030343059301306072A8648CE3D020106082A8648CE3D03010703420004C5A11656398A9216FC72BB28BA4A698539BF8F472B066CC8402A9DA49FD02433EBB54767470F5D877A9C4E2E9B7047D25AF85BCE203DC64551EAD9DB71EBB833A3663064301D0603551D0E0416041493237066C51DCEC4AB1C2BAD84C1F3E71DCE6067301F0603551D230418301680144BBD872611AD1C89CF0458BE70D2088C6B1623B730120603551D130101FF040830060101FF020100300E0603551D0F0101FF040403020106300A06082A8648CE3D040302034800304502207FB540C43F46961624BD132548B44ADF04B661718FE42C32BA5F9AD40C706AB5022100FAC5A67DDCD5C7F79158A4190568995BAEC753E27A954A4E3221F79E4A60C2F1 |
|---|
}}
- Select Attestation: Indirect and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{65{ | Credential ID
7B3DAB1F7E1F42A98832131E6ED8385130E087C235B130D7ABCC26D972C640F3 RP ID
webauthntest.identitystandards.io AAGUID
EE041BCE-25E5-4CDB-8F86-897FD6418464 Credential Registration Data [more details]
Key Type: EC
Discoverable Credential: true
Attestation Type: packed
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1570 Last Authentication Data [more details]
No authentications |
|---|
If registration worked, click on "Credential Registration Data [more details]" and copy-paste the content of the dialogue: | Require Resident Key
true Authenticator Data
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1570 Authenticator Data in Hex
0B997CCCEB3AEB29C55C94A894B11CF01A24B4C8AE706F328CC2EA8CEBC4AD5C4100000622EE041BCE25E54CDB8F86897FD641846400207B3DAB1F7E1F42A98832131E6ED8385130E087C235B130D7ABCC26D972C640F3A501020326200121582082028C12E0F8100B2C0471646BEB031054D131FC37EA6D6633A16E72DB8012A3225820349A6370DB2045F0F8F6D48D6EA9A005748AC7084A22414A72A7367DC9A01437 Public Key
EC key: A501020326200121582082028C12E0F8100B2C0471646BEB031054D131FC37EA6D6633A16E72DB8012A3225820349A6370DB2045F0F8F6D48D6EA9A005748AC7084A22414A72A7367DC9A01437 Extension Data
No extension data Attestation Statement Chain
[{"version":3,"subject":"/C=US/O=Feitian Technologies/OU=Authenticator Attestation/CN=FT FIDO2 0430","issuer":"/C=US/O=Feitian Technologies/CN=Feitian FIDO CA 04","extAaguid":{"critical":false,"oid":"1.3.6.1.4.1.45724.1.1.4","vidx":942}},{"version":3,"subject":"/C=US/O=Feitian Technologies/CN=Feitian FIDO CA 04","issuer":"/C=US/O=Feitian Technologies/CN=Feitian FIDO Root CA"}] Attestation Statement in Hex
A363616C6726637369675847304502200220BFF07E73141EC383950BA398B58EBAC4F80832B70DAEC06813E8995FCF26022100A01EBFF3AA8EA01C2355F052D7BA2D968A32245253ED764EB9A1F6558E96D387637835638259023F3082023B308201E1A00302010202101DF2B55A51DC4B6885A3D99E697FED12300A06082A8648CE3D0403023049310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F67696573311B301906035504030C124665697469616E204649444F2043412030343020170D3138303532313030303030305A180F32303333303532303233353935395A3068310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F6769657331223020060355040B0C1941757468656E74696361746F72204174746573746174696F6E3116301406035504030C0D4654204649444F3220303433303059301306072A8648CE3D020106082A8648CE3D03010703420004B27E0E8E39001F54EC9B6F4FE8841903764520A876EB698D3CC00D7D5B4DC3CCD95632A31A13ACBD67F38F3D62B2A5A0DC0CA52896400DC9AD39788BEA288045A38189308186301D0603551D0E04160414DD3244171A67ABBF52200773D13CCF3796AE77B1301F0603551D2304183016801493237066C51DCEC4AB1C2BAD84C1F3E71DCE6067300C0603551D130101FF040230003013060B2B0601040182E51C0201010404030204303021060B2B0601040182E51C01010404120410EE041BCE25E54CDB8F86897FD6418464300A06082A8648CE3D040302034800304502203F16E910B2A1BD7FAC33D43DA681B9663867DD6FA2D7CB9D274707F7FCF1B1B1022100A33BB88152391FC652BB9B7DE31832E5026B9AD3E37AC94F25A6F44EABF344D65901FE308201FA308201A0A003020102021018152B41B743AE6DB41599C3B17D8209300A06082A8648CE3D040302304B310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F67696573311D301B06035504030C144665697469616E204649444F20526F6F742043413020170D3138303532303030303030305A180F32303338303531393233353935395A3049310B3009060355040613025553311D301B060355040A0C144665697469616E20546563686E6F6C6F67696573311B301906035504030C124665697469616E204649444F2043412030343059301306072A8648CE3D020106082A8648CE3D03010703420004C5A11656398A9216FC72BB28BA4A698539BF8F472B066CC8402A9DA49FD02433EBB54767470F5D877A9C4E2E9B7047D25AF85BCE203DC64551EAD9DB71EBB833A3663064301D0603551D0E0416041493237066C51DCEC4AB1C2BAD84C1F3E71DCE6067301F0603551D230418301680144BBD872611AD1C89CF0458BE70D2088C6B1623B730120603551D130101FF040830060101FF020100300E0603551D0F0101FF040403020106300A06082A8648CE3D040302034800304502207FB540C43F46961624BD132548B44ADF04B661718FE42C32BA5F9AD40C706AB5022100FAC5A67DDCD5C7F79158A4190568995BAEC753E27A954A4E3221F79E4A60C2F1 |
|---|
}}
- Select Attestation: None and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{70{ | Credential ID
87885C41E418171A07E37A44C748D366915488DD1F78F860A197E99CFB62D9E0 RP ID
webauthntest.identitystandards.io AAGUID
EE041BCE-25E5-4CDB-8F86-897FD6418464 Credential Registration Data [more details]
Key Type: EC
Discoverable Credential: true
Attestation Type: none (unverified)
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1574 Last Authentication Data [more details]
No authentications |
|---|
}}
- If none of the previous four tries worked:
- Select Attestation: Undefined and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
- Otherwise, skip this step.
Copy-paste the result on the right:
Put Unsupported if there was an error{75{ | (skipped) |
|---|
}}
- If Attestation: Direct worked, select it. Otherwise, if Attestation: Indirect worked, select it. Otherwise, select Attestation: Undefined.
Test CredProtect Extension
- Select CredProtect Extension: UVOptional and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{80{ | Credential ID
09B22C388CCC2D87CCED3BE2F39A1DDD3E45EDDDDA7AB77EE008D75AA41596B0 RP ID
webauthntest.identitystandards.io AAGUID
EE041BCE-25E5-4CDB-8F86-897FD6418464 Credential Registration Data [more details]
Key Type: EC
Discoverable Credential: true
Attestation Type: packed
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1769 Last Authentication Data [more details]
No authentications |
|---|
}}
- Select CredProtect Extension: UVOptionalWithCredIDList and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{85{ | Credential ID
FAAFB7E5186E2626CE5CF23380B4D4B2A6AE732679F56AEEE3B848929EDDE82F RP ID
webauthntest.identitystandards.io AAGUID
EE041BCE-25E5-4CDB-8F86-897FD6418464 Credential Registration Data [more details]
Key Type: EC
Discoverable Credential: true
Attestation Type: packed
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1779 Last Authentication Data [more details]
No authentications |
|---|
}}
- Select CredProtect Extension: UVRequired and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{90{ | Credential ID
14C6913D159EADDEEF4325A02DD67888748786A72D3F44CEB9AAF85F16692356 RP ID
webauthntest.identitystandards.io AAGUID
EE041BCE-25E5-4CDB-8F86-897FD6418464 Credential Registration Data [more details]
Key Type: EC
Discoverable Credential: true
Attestation Type: packed
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1829 Last Authentication Data [more details]
No authentications |
|---|
}}
- If none of the previous three tries worked:
- Select CredProtect Extension: Undefined and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
- Otherwise, skip this step.
Copy-paste the result on the right:
Put Unsupported if there was an error{95{ | (skipped) |
|---|
}}
- Select CredProtect Extension: Undefined (if not selected already).
Test cryptography
- Uncheck all the following checkboxes: Use ES256, Use ES384, Use ES512, Use RS256, Use EdDSA.
- Check Use ES256 and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{100{ | Credential ID
EAC0845158B8830C915E2AD81FD1E3F4BDF6CA7ABC162606EC4536EBEEE0A94D RP ID
webauthntest.identitystandards.io AAGUID
EE041BCE-25E5-4CDB-8F86-897FD6418464 Credential Registration Data [more details]
Key Type: EC
Discoverable Credential: true
Attestation Type: packed
UP=1, UV=0, BE=0, BS=0, AT=1, ED=0, SignCount=1999 Last Authentication Data [more details]
No authentications |
|---|
}}
- Uncheck Use ES256, check Use ES384 and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{105{ | Unsupported |
|---|
}}
- Uncheck Use ES384, check Use ES512 and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{110{ | Unsupported |
|---|
}}
- Uncheck Use ES512, check Use RS256 and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{115{ | Unsupported |
|---|
}}
- Uncheck Use RS256, check Use EdDSA
- and click CREATE.
- Follow the requested steps to create a passkey, then copy-paste the result from the web app.
Copy-paste the result on the right:
Put Unsupported if there was an error{120{ | Unsupported |
|---|
}}
Conclusion
Do you have any additional observations or comments related to the entire procedure:{125{ | The key obviously ignores the user verification flag and never performs user verification. But when I use the key in Google Chrome, it forces me to set up a PIN when User Verification is set to Required. |
|---|
}}
- Please do not forget to paste any pending screenshots in the above tables.
- You may also paste the screenshot with the passkey(s) created during this test. The list of created passkeys is usually shown along with platform or browser passkey options that you were already asked to screenshot.
Thank you!
