If GÉANT, as Data controller (DC), engage another organization as Data processor (DP) to process personal data on behalf of GÉANT, requirements defined in Article 28. of GDPR should be met and appropriate Data processing agreement (DPA) should be signed between GÉANT and DP.
Outline of DPA
Legal framework
DPA should contained common legal framework based on GDPR requirements.
Security measures (DRAFT)
DPA should define security measures in order to ensure protection of personal data. When properly implemented they can provide assurance that DP can provide adequate protection of rights of data subjects. Security measures are service specific and depends on architecture, scope and other factors. Here is list of some general security measures which can be used as reminder. Chosen and applicable measures should be elaborated in more details as appropriate.
- personnel - trained in data security, they signed AUP or Statement of Confidentiality concerning personal data
- access management - only authorized personnel can access data, strong password or 2-factor authentication are used for access, access to data are logged
- access protection - firwewall or ACL protection
- stored data protection - pseudonymisation, anonymisation, database encryption, hard disk and removable media encryption, data encryption
- data transfer protection - during transfer data are protected with secure encryption methods such as TLS, VPN, WPA2 for wireless, SSH
- vulnerability management - software are timely patched, regular vulnerability scanning or penetration testing of applications or systems
- malware protection - antivirus, email antimalware protection, education of personnel
- data leak protection - IDS, continuous monitoring, removable media policy
- regular backups - stored on safe place, encrypted, restore regularly checked
- incident management - quick incident response, timely reporting all incident to data controller
- DDOS protection - network or application
DPA approval procedure
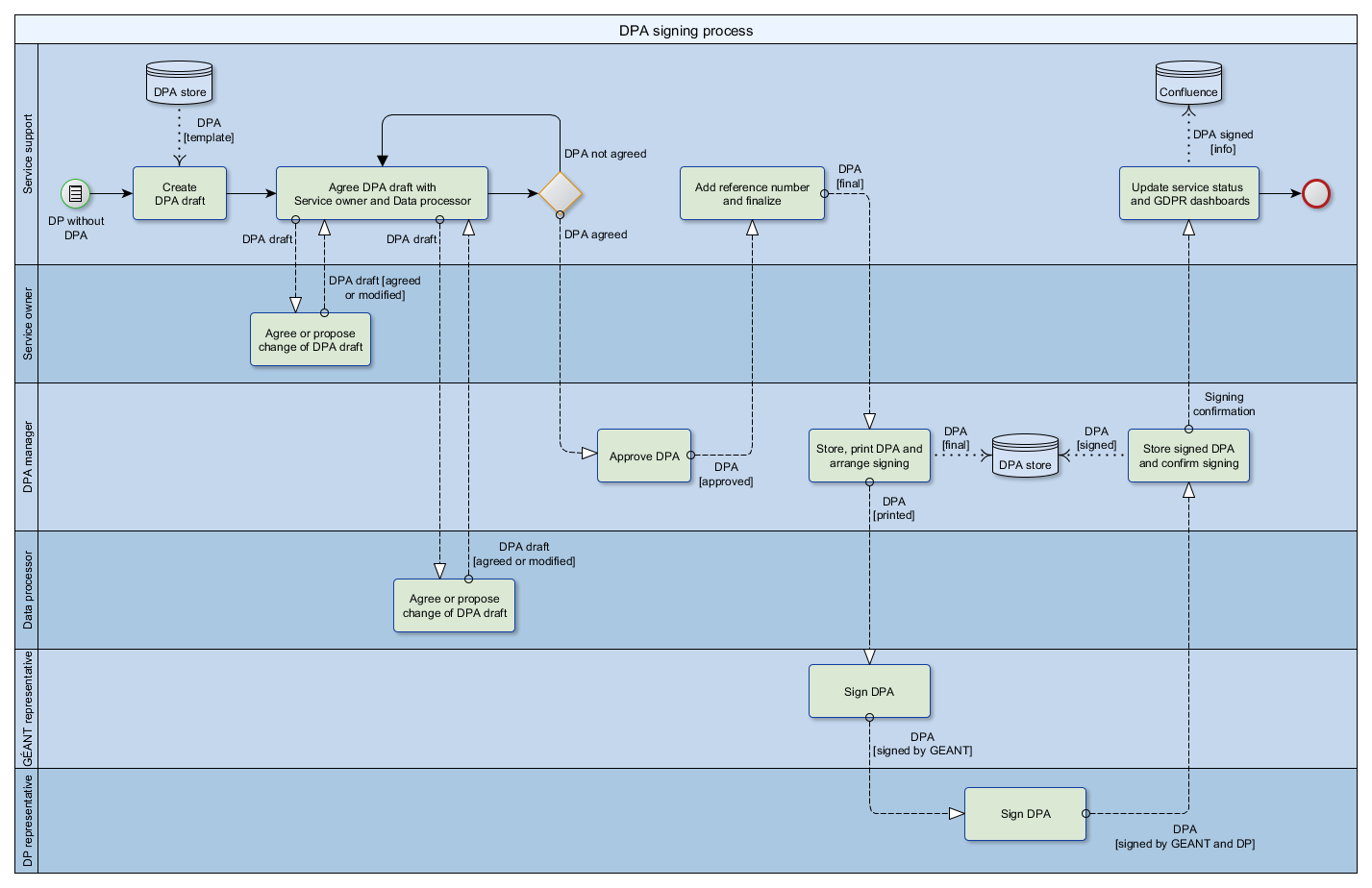
Process . Process of drafting, approving and signing of DPA is shown on the following figure.
Roles and their activities
There are several roles involved in this process and each of them perform the following activities:
...