Requirement
|
Overview
As previously mentioned in the precedent article, when you log into a network equipment such as a router, you tend to have some automatic reflex. You usually:
- Check router configuration: show run or sh conf
- Check ipv4 / ipv6 / or LFIB forwarding table
- So you basically issue diagnosis, troubleshooting command
- An then you want to configure the router
Article objective
In this article, we will focus on the 3rd bullet point and will present you freeRouter available diagnosis command. They are grouped into 5 categories:
- show
- view
- watch
- display
- differ
Basically these commands are accessed through freeRouter user mode. If you need to use them from config mode, please use the "do" keyword.
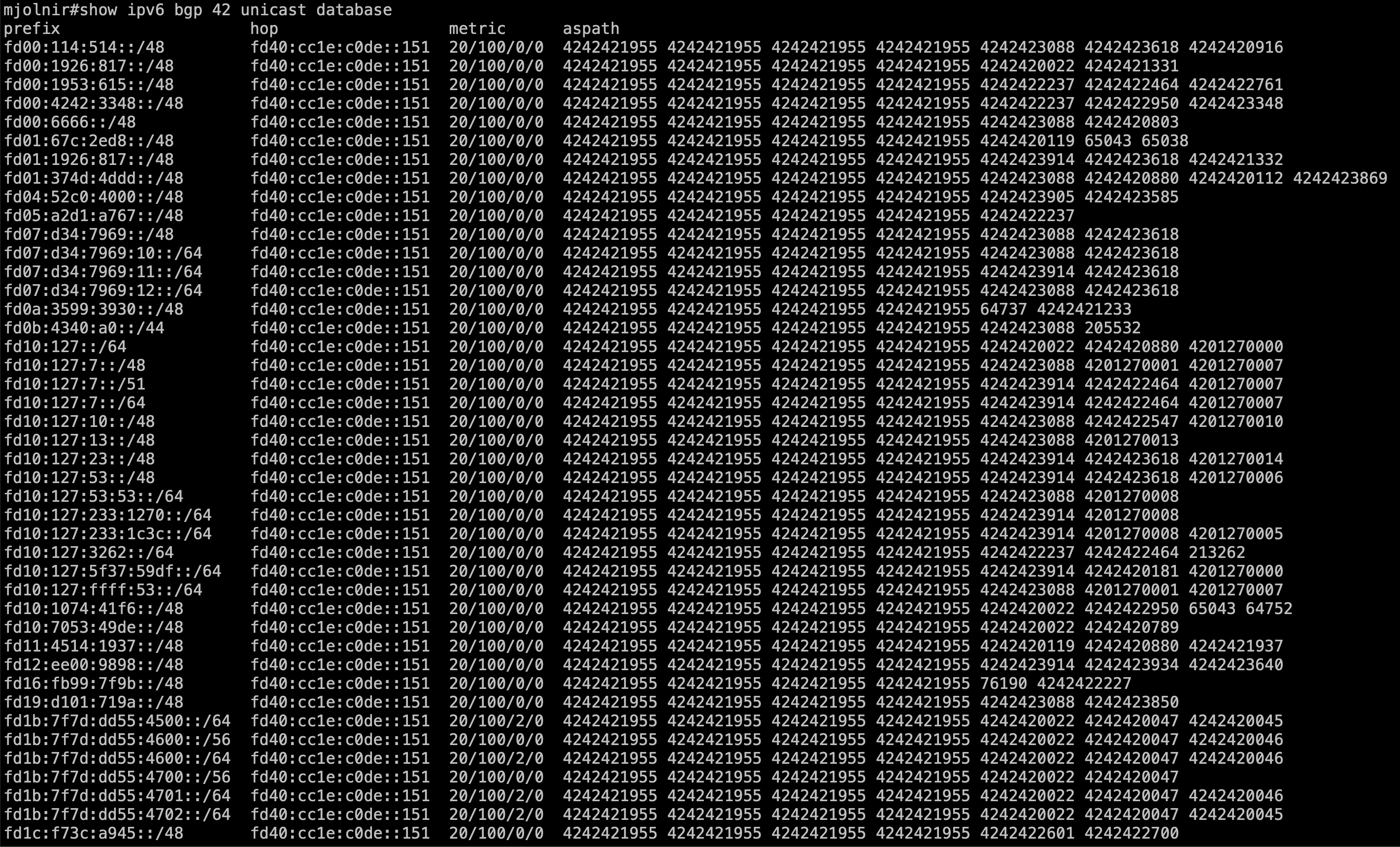
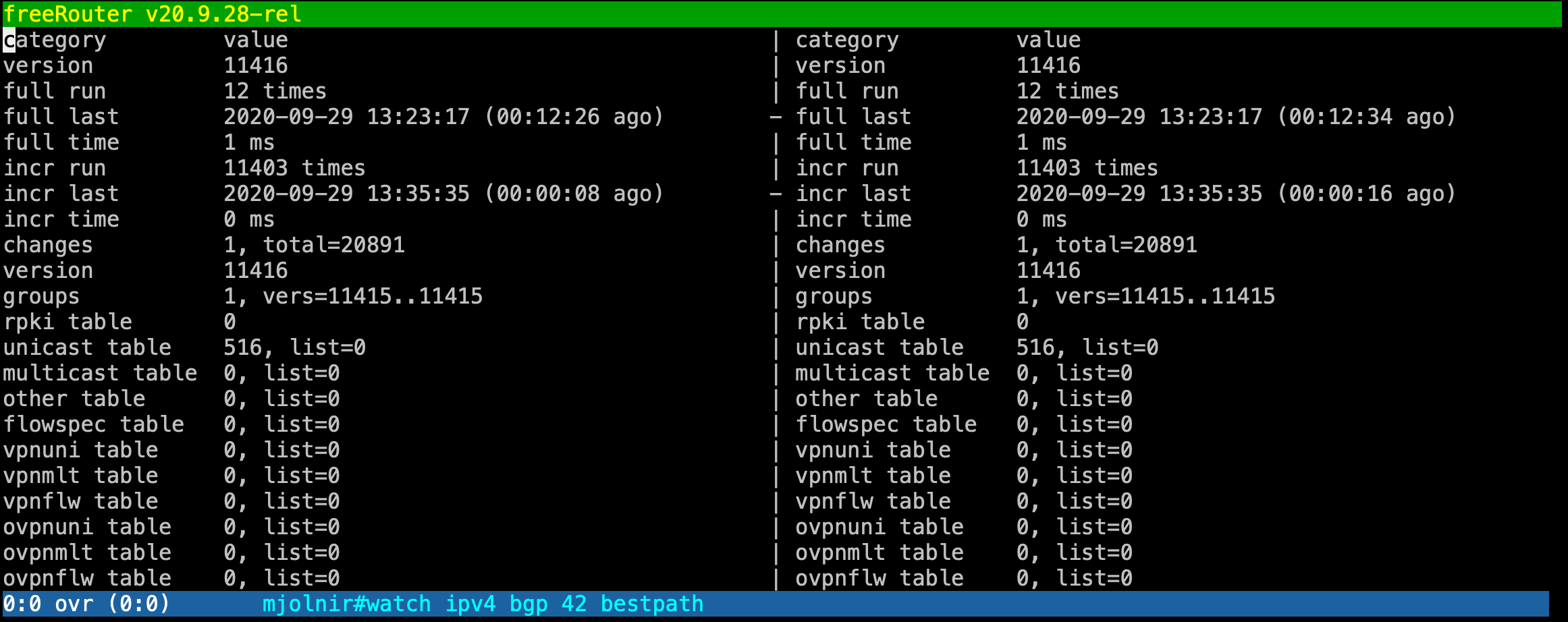
[ #002 ] - "show/view/watch/display/differ"
Discussion
show/view/watch/display/differ is pretty unique to freeRouter, and is really meant to provide you the best user experience as a network operator ! These command have proven to be helpful, especially if you deal with huge feed. However, be careful when you are working with very big output such BGP full feed. This won't crash the router of course as we used to when we issued "debug ip packet" but it will for sure imply a high CPU usage due to regular refresh at the control plane level.
Conclusion
In this 2nd article:
- We presented freeRouter show/watch/display/differ diagnisis command
- These are very useful when you have to deal with huge command output buffer.
Final words
As said, these are diagnosis commands are specific to freeRouter. 2 decades of know how and network experience have been pushed into these feature codes. These have been developed for one purpose:
"Provide a unique operation experience to network engineers"
Feel free to try and use them according to your environment taste!
Last but not least, you can play with these different mode from this sandbox:
ssh dl.nop.hu -l random_user Warning: Permanently added 'dl.nop.hu,193.224.23.5' (RSA) to the list of known hosts. random_user@dl.nop.hu's password: XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX XXXX XXXXX XXX XXX XXX XX XX XXXX XXXXXXXXXXXXXXXXXXX XXXX XXXX XX XXXX XX XXXX XX XX XX XXXX XXXXX/~~~~~~\XXXXXX XXXX X XXX XX XXXX XX XXXX XX XX XX XXXX XXXX| player |XXXXX XXXX XX XX XX XXXX XX XXX XX XXXX XXXXX\______/XXXXXX XXXX XXX X XX XXXX XX XXXXXXX XX XX XXXX XXXXXXXXXXXXXXXXXXX XXXX XXXX XX XXXX XX XXXXXXX XX XX XXXX XXXXXXXXXXXXXXXXXXX XXXX XXXXX XXX XXX XXX XXX XX XXX XXXXXXXXXXXXXXXXXXXX XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX welcome line ready menu lab: # - reboot router1 $ - reboot router2 % - reboot router3 1 - connect to router1 2 - connect to router2 3 - connect to router3 ^ - rebuild routers l - connect to lg.nop.dn42 x - exit choose:l - telnet 172.23.199.110 23 /telnet - connecting to 172.23.199.110 23 - securing connection hi there! try the following: show ipv4 route dn42 show ipv6 route dn42 show ipv4 bgp 65535 vpnuni summary show ipv6 bgp 65535 vpnuni summary show ipv4 bgp 65535 vpnuni database show ipv6 bgp 65535 vpnuni database show ipv4 bgp 65535 vpnuni allroute <prefix> 65535:42 show ipv6 bgp 65535 vpnuni allroute <prefix> 65535:42 show ipv4 logger 42 flapstat 10 show ipv6 logger 42 flapstat 10 show ipv4 bgp 65535 vpnuni flapstat 10 show ipv6 bgp 65535 vpnuni flapstat 10 show ipv4 bgp 65535 vpnuni flappath <prefix> 65535:42 show ipv6 bgp 65535 vpnuni flappath <prefix> 65535:42 have fun! mc36 welcome line ready player-dn42> player-dn42> ...
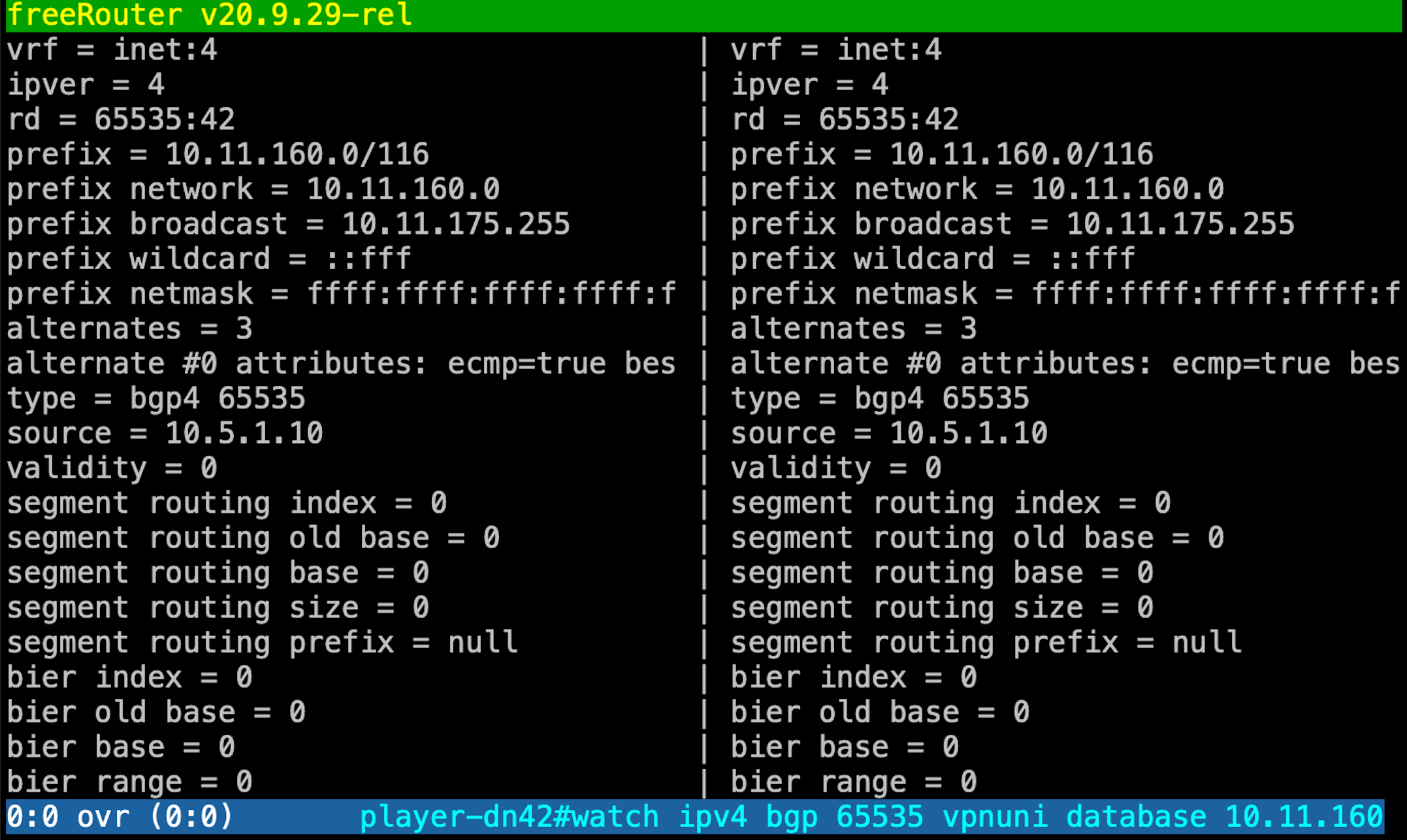
Then issue a "diff" command:
player-dn42>diff ipv4 bgp 65535 vpnuni database 10.11.160.0/20 65535:42 ...
You'll be rewarded by this diff out related to the command which means:
"show me the prefix status of 10.11.160.0/20 within BGP process 65535 with rd: 65535:42"
After a quick look at VRF definition indicates that rd 65535:42 is tied to VRF dn42:
player-dn42>sh start vrf vrf definition dn42 rd 65535:42 rt-import 65535:42 rt-export 65535:42 source4route all source6route all mdt4 mdt6 exit vrf definition rtbh rd 65535:666 rt-import 65535:666 rt-export 65535:666 exit vrf definition vpn rd 65535:1 rt-import 65535:1 rt-export 65535:1 mdt4 mdt6 exit ...
In order to exit the sandbox session use the following escape sequence: Ctrl-c + Ctrl-x